How to protect my Android or iPhone from ransomware in 2025
It's Anti-Ransomware Day - time to make sure your iPhone or Android can't get hacked or broken into. Check this guide!
Many still think ransomware is only directed at businesses, but Wired called it a “ransomware epidemic” in 2024, suggesting that this problem will spread far and wide, also targeting people and their phones. Attackers no longer only target high-profile businesses to extort millions of dollars, but also individuals. The aim of hackers targeting your personal Android or iOS device is to either get their hands on your private data for extortion purposes, or to abuse your data, for instance, to maliciously get access to your digital identity, to your mailbox, your PayPal, your Amazon, or even your bank accounts.
If you’ve never taken care of the security of smartphone or your digital identity, it’s not too late! You can check here whether your accounts have been hacked and install apps that scan for viruses and malicious apps on your Android and iPhone. But more on this in this guide!
So, how can you protect your Android or iPhone from ransomware? Let’s find out!
Best way to protect yourself
10 Steps to keep your phone safe from ransomware


Can you tick these ten steps? If yes, your phone uses state-of-the-art protection against ransomware
We’ve summarized 10 easy steps how you can prevent your smartphone from getting hacked:
1. Keep your device updated
- Why: Security vulnerabilities are constantly being discovered. Updates patch these holes.
- Android: Settings → System → Software Update → Check for Updates
- iPhone: Settings → General → Software Update → Install if available
2. Install only trusted apps, the fewer, the better
- Why: Most apps track you and use your data. You also need to be careful not to download malicious apps.
- Android & iPhone: Get only the apps you need, and deinstall apps that you no longer need.
3. Limit app permissions
- Why: Apps with unnecessary permissions can be exploited to lock or ransom your data. Many apps grant themselves access to your location, your contacts, your photos - which they don’t even need.
- Android: Settings → Apps → App Permissions → Review and restrict.
- iPhone: Settings → Privacy & Security → Review per category (e.g., Photos, Files).
4. Use a mobile security app
- Why: Security apps offer ransomware protection, they scan and block maliciously looking software.
- Trusted apps on Android: Bitdefender Mobile Security, Norton Mobile, Malwarebytes
- Trusted apps on iPhone: Lookout, Norton Mobile, iVerify (for iOS-specific hardening)
5. Back up regularly
- Why: If ransomware locks your phone, a backup ensures you don’t lose your data.
- Android: Use Google Backup: Settings → Google → Backup → Enable - Use cloud services like OneDrive, Dropbox for extra safety
- iPhone: Use iCloud: Settings → [Your Name] → iCloud → iCloud Backup - Or back up locally via iTunes/Finder
6. Never click on unsafe links & attachments
- Why: Phishing messages and malicious links are the primary infection vector.
- Tips: 1. Don’t click on unknown links in SMS, WhatsApp, or email. 2. Avoid downloading attachments from unknown contacts. 3. If unsure, preview the link or use a URL checker (like VirusTotal). 4. Read more on how to prevent phishing in Tuta Mail.
7. Enable Play Protect or similar
- Why: These built-in services scan apps for malware.
- Android: Google Play Store → Tap profile → Play Protect → Turn on & Scan
- iPhone: iOS doesn’t have Play Protect, but the App Store’s strict review helps. Use a security app for added protection.
8. Use strong lock-screen security
- Why: Ransomware attackers can also try to lock access to your device.
- How: Use biometrics (Face ID, fingerprint) and a strong PIN or password to lock down your phone; use pin or biometrics also for important apps like Tuta Mail. Disable Smart Lock features on Android that might auto-unlock your device in certain locations.
9. Avoid public Wi-Fi or use a VPN
- Why: Public networks can be spoofed or intercepted to push malicious payloads.
- How: Don’t join unknown public Wi-Fi networks. Use a trusted VPN (like Mullvad, or Bitdefender VPN) when connecting to a public Wi-Fi.
10. Know the signs of a ransomware attack
-
Symptoms that you’ve been attacked:
-
Sudden lock screen demanding payment
-
Inaccessible files
-
Apps crashing unexpectedly
-
Unusual behavior after installing a new app
-
What to do to stay ahead of the ransomware attacker:
-
Disconnect from the internet.
-
Remove the suspicious app.
-
Boot into safe mode (Android).
-
Restore from backup.
-
Contact support (Google, Apple, or your AV provider).
Most important attack vectors
By following the steps above to defend your device against ransomware attacks, you’ve already achieved a lot to make sure your Android or iPhone can’t fall victim to an attack. However, there are also factors to consider that could make you the target of a ransomware attack. So it’s important to know the most important attack vectors:
- Using phones that no longer receive OS updates
- Using outdated software, apps, or browsers
- Not having a proper backup plan
- Not paying attention when receiving unexpected messages or emails
Ransomware often starts with an email
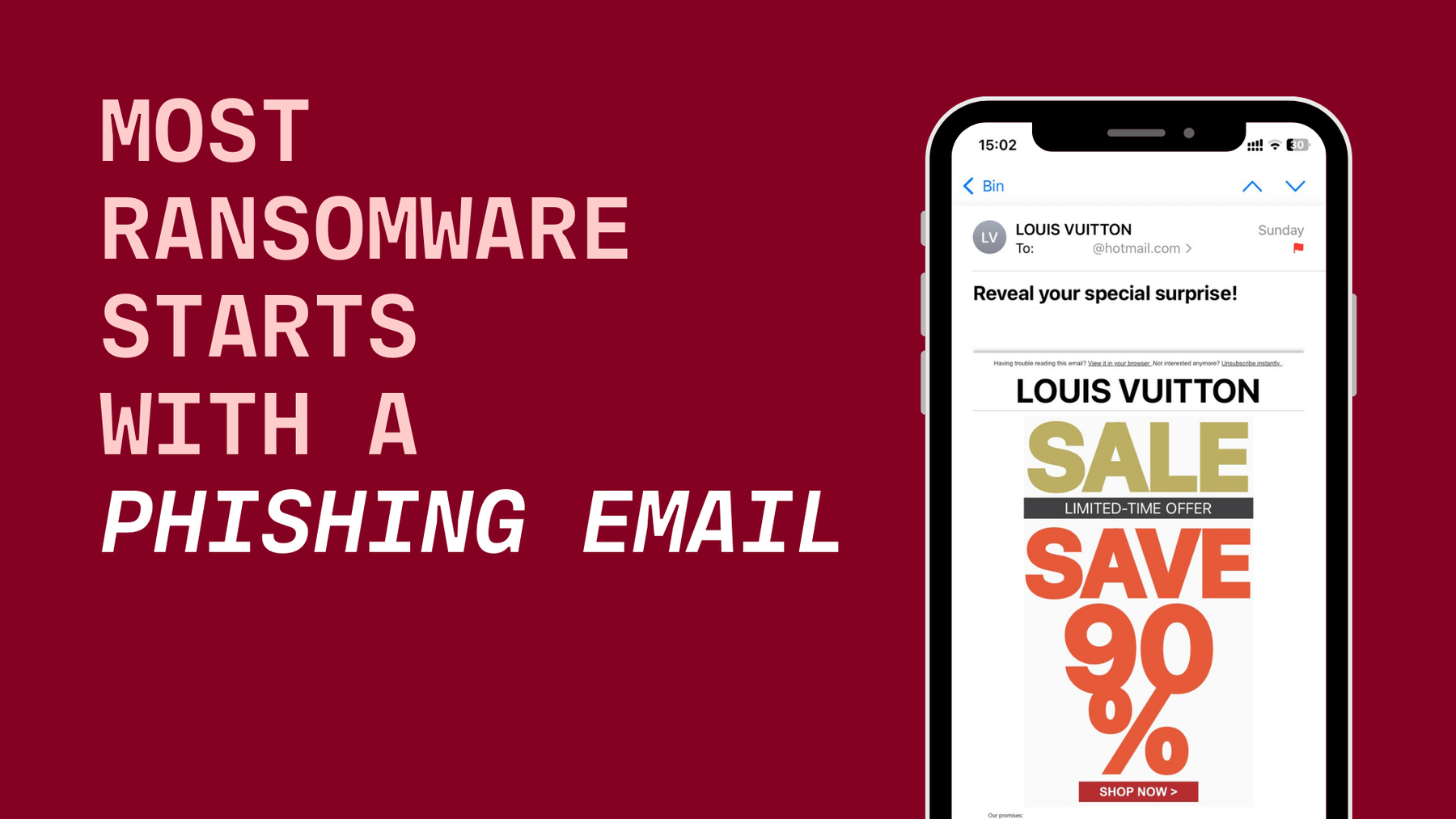

Phishing email: often the beginning of a ransomware attack
Most ransomware attacks start with an email. Newer attack methods include attacks via the Google Calendar, via QR codes - so called quishing attacks, or via whatsApp messages.
Yet, email is still the prime target for most ransomware attackers. The federated email system makes it rather easy for malicious attackers to send malicious phishing emails which either contain phishing links or malicious attachments. The aim of the ransomware attacker is to phish users’ login credentials or make them download attachments that include code such as viruses and can infect the user’s system.
The tactics of the attackers are usually always the same and should be easy to spot, (to learn how read our guide on how to not fall victim to phishing emails). Attackers spoof email domains of known companies (e.g. amaz0n.com), disguising these emails as legitimate. They create a sense of urgency (e.g. confirm your login now or lose access) to make people enter their login credentials on malicious sites.
So whether on your phone or on your desktop, the key take-away to keep yourself safe from ransomware is to never-ever click unsafe links and to never-ever download and open malicious attachments.
Do not leave your phone unattended
When you are not at home, never leave your device unattended. Even if you are at semi-private events such as a friend’s party or at the office, make sure that your Android or iPhone is always protected against unauthorised access and manipulation.
In case you’ve lost your phone, or it got stolen, lock it down! On Android, you can use the Find my device feature or Google’s theft protection feature to either find where it is or to lock down and erase the data on the phone to make sure it does not get in the wrong hands. On iOS, you can use Lost Mode in iCloud to find a lost iPhone and Stolen Device Protection to safeguard all your data in case your iPhone got stolen. It’s important for these use-cases to only use apps from trusted providers so even as an open source fan, it makes sense here to use Google’s and Apple’s own apps. Once locked, you also need to make sure that your SIM card gets blocked. Do this last, as otherwise you will not be able to lock down your phone.
If your stolen phone is connected to the internet, it could be possible to find it via the network operator with your unique IMEI number. Write down this 15-digit number, which you can find in the Settings of your phone or by dialing *#06#.
Is it even necessary to protect your iPhone?

Are iPhones better protected than Android devices?
Some people will argue that iPhones are more secure due to the fact that Apple focuses a lot on security and, for instance, limits app developers to only publishing their apps via the App Store which is under Apple’s control and every app update is checked by the Apple team. Though, malicious apps also sneak into the App Store as our detailed guide on iPhone security tips explains.
In addition, with the US and EU cracking down on Apple’s monopoly, it is becoming more obvious by the day that Apple’s strict policy on preventing app side-loading is not done for improving your security, but for protecting Apple’s own profits. And the same is now happening with another tech giant: Google also plans to block side-loading on Android devices, following Apple’s example.
Altogether, it’s fair to say that there are more ransomware attacks on Android (possibly because there are more Android devices), but targeting iPhone users is also becoming more lucrative to attackers as these usually earn more money. So yes, it is necessary to protect your iPhone from ransomware attacks, and you can do so by following the steps explained above!
Security above all else?
When starting to learn about digital hygiene and phone security, it might all seem overwhelming to many. But by staying alert to potential threats like malicious links and attachments, always updating your apps and your phone’s OS, and by using two-factor authentication, best with a hardware key, you can increase your security a lot, and it is less effort than you might think. Plus, it can be done easily on the couch whenever you are bored of scrolling through your social feed. 😉
Last, but not least, the best way to never fall for phishing emails that could lead to ransomware attacks is to use a secure email provider like Tuta Mail.
So if you do one thing to improve your security on Anti Ransomware Day, sign up for Tuta Mail!