Essential iPhone security tips to protect your private data.
Apple's closed software ecosystem doesn't provide complete protection from viruses or hackers. It's up to you to stay alert.
Since it’s initial launch in 2007 Apple’s iPhone has become one of the most popular smartphones in the world. Sleek design and a reputation for being more secure than competitors make them the go-to choice for more than one billion users. Much like their Mac computer line the iPhone has proven itself to be a secure mobile device even with its out-of-the-box privacy and security settings. But where does this status come from? Are Apple’s devices really more secure than Google’s Android alternative? Are there viruses which target iPhones and if so what can you do to keep your iOS device safe and your data secure?
As privacy and security experts we want to increase knowledge and awareness on iOS threats and in this article we will walk you through the ins and outs of the iPhone’s security model and why they seem to be better protected against malware and other viruses.
Are iPhones more secure than Android phones?
This is a complicated question that is bound to start a number of online arguments, but if we take two stock devices, one iPhone and one Android phone, and compare them based upon their out-of-the-box protections the iPhone is a more secure device.
This is largely to do with the way in which Apple has created their own closed ecosystem for iOS/Mac devices and software. iPhones and iPads come with a number of productivity apps pre-installed and users don’t necessarily need to go out and search for new software for their devices. By taking these steps Apple can ensure that their official software is secure.
The next step which Apple has taken to harden the security of iOS devices is by forcing its developers to release their apps through the Apple App Store rather than allowing unregulated sideloading of software. While this walled garden approach is a major burden on app developers it does guarantee a degree of security as the available software faces a higher degree of scrutiny. Of course, this system is not without fail and in 2024 a fake password manager did sneak onto the App Store, but Apple was quick in removing it.


A fake password manager was briefly available for download in the Apple App Store despite being a fraudulent version of LastPass.
These steps do not mean that a hardened Android device cannot provide better security and privacy than an iPhone, GrapheneOS is a great example of a secure mobile platform, but for the average user Apple makes a great starting point.
Boot ROM Protections and Secure Enclave
Beyond maintaining application security through their walled-garden approach to software distribution for iOS, Apple has also introduced two major features which are supposed to maintain the integrity and security of their iPhone devices.
The first of these is the Boot process protections. When an iOS device is powered on, code contained in the Boot ROM is run to check against the Apple certificate authority to determine the integrity of the bootloader before it is allowed to be loaded on the device.
The second measure taken by Apple they have called Secure Enclave. Secure Enclave is deployed on iOS and MacOS devices as a secure buffer which protects personal data stored on the devices in the event of an application kernel compromise.
These are just two ways that Apple is introducing extra security measures to protect their users’ data.
Can iPhones get viruses?
Simply put, yes, iPhones can get viruses. While Apple has taken a number of steps to create a secure ecosystem for their devices, and iOS malware is less common than Android malware, you can still end up with a virus on your iPhone.
Due to their growth in popularity, use by notable individuals and celebrities, and even their usage by top officials in US government agencies the iPhone has long had a target painted on its back. By releasing regular updates to their device operating systems and running a number of bug bounty programs, Apple does attempt to stay on top of zero-day exploits and malware.
Apple releases its software directly to end user devices and they do so in a completely closed source way. This means that not everyone can peek at how exactly iOS software works. Their goal is that this element of secrecy protects their software from exploits, but this is not the case. In 2023 Apple released emergency security updates for 20 zero-day vulnerabilities and at the time of writing have fixed 3 vulnerabilities in 2024.
Every cryptographer worth their salt will tell you that security through obscurity alone cannot create a secure system of communications. The National Institute of Standards and Technology (NIST) recommends avoiding this practice “System security should not depend on the secrecy of the implementation or its components.” Unfortunately, Apple continues to release their proprietary software closed source rather than in a publicly available open source format which would allow security researchers to review and critique certain aspects of their security designs.
We cannot say definitively that releasing their software through open source standards would lead to fewer viruses on iOS, iOS malware is rare in comparison to Android or Windows malware, but it would inspire a greater degree of trust in what is actually running on Apple devices. This would absolutely increase the trust in the privacy which Apple claims to provide their iPhone users.
Why are there less iPhone viruses than on Android?
Generally, there are less iPhone viruses due to the way that software for iPhones can be released. Currently, outside of the EU, it is only possible to install software on an iPhone or iPad through Apple’s proprietary App Store. As mentioned above, this introduces a gatekeeper which can act as a bouncer for malware trying to sneak into the smartphones. However, the gatekeeper function of Apple is also being criticized under the new Digital Markets Act (DAM) so that Apple is now forced to give people on iPhones a choice to change their default browser from Safari to another one.
While the gatekeeper function of Apple can have benefits, it for sure has also disadvantages. In addition, this gatekeeper isn’t always wary and hackers are smart, through social engineering hackers have learned to target app developers as potential ways to get malicious code into the App Store which was the case with the spread of the XCodeGhost malware in 2015.
With Android being open source and also being catered to a number of different device manufacturers there is simply easier access to potential vulnerabilities. There is also the game of numbers and there are far more Android users world wide than Apple users, so there is financial incentive in trying to target these users.
There is a noticeable increase in malware which targets iPhones which have been jailbroken. These devices have escaped Apple’s walled garden and with that freedom does come an increased number of threats and a likely smaller development team working to counteract them.

By keeping your iPhone updated with the latest operating system and security software you are already taking active steps to protect your device and data.
Types of iPhone Malware and Attacks and how to prevent them
With Apple devices becoming a more lucrative target for malicious actors, there has been a rise in malware development for iPhones. However, this doesn’t mean that the majority of attacks are novel, some major threats still follow the tried and true method of social engineering through phishing or smishing.
Phishing/Smishing
We have all seen those phishing messages which claim that you will be locked out of your bank account in 24-hours unless you CLICK THIS LINK and enter your login information to reactivate it.
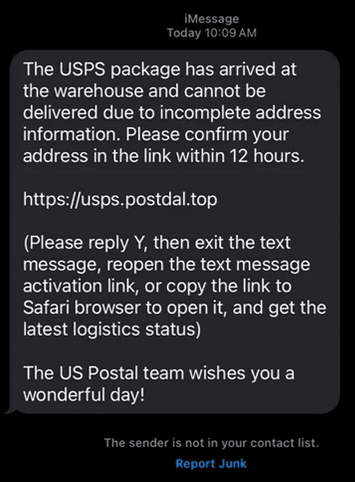

Phishing messages come in many flavors. A popular version is a fake postal delivery message. There is an entire subreddit dedicated to these messages, r/phishing. Image from Netcraft
While this is not an iPhone specific issue, it can be used to target Apple users iCloud accounts. When you see celebrity data leaked across social media, often this is caused by a successful phishing attack. Once these login credentials are stolen the attacker can reset passwords, download data, or steal payment information.
On iOS devices, you might receive shady looking SMS messages in your Messages app trying to prompt you to visit a website and try to login. Sometimes these can be iMessage messages as well. What is important if you receive these messages is to keep calm, don’t click any links or download files and don’t be fooled by the fake sense of urgency.
If you have received a phishing iMessage you can report it and block the sender by following these steps provided by Apple.
One great way of protecting yourself against these kinds of phishing attacks is by using Apple’s message filter for unknown senders. These can be enabled by following these steps:
- Click on Settings > Messages
- Scroll to Message Filtering and enable Filter Unknown Senders
This feature is great because it will sort incoming messages from numbers not stored in your contacts lists in their own folder for review.Best of all, you cannot open any links by messages sent to you by unknown senders without first adding them as a contact or sending them a reply.
A similar feature is also available for incoming calls.
When it comes to these messages, make sure you stay vigilant and get in the habit of not clicking links by default. As always it is also a best practice to make sure that you have enabled 2FA on your AppleID.
Apple has also introduced passkey support and by configuring passkeys as your primary means of authentication you can stay one step ahead of fraudsters who are trying to steal your login information.
Viruses via email and risks
The Message app is not the only way that attackers might try to steal your personal information through sending phishing mails. Email is another prime source of device infection and can be the ground zero of many cyber attacks. As with Message, make sure not to click links from unknown senders.
If files cannot be loaded on your device they may be delivered through your mail client. All iPhones come with Apple Mail installed and many users take advantage of this by moving all of their email accounts into this single mailbox. While convenient, Apple Mail does not provide the same degree of security that other email providers can.
To avoid getting flooded with unwanted spam it is important to take advantage of email aliases. Apple offers this service with their iCloud private addresses, but there are many other secure options available like DuckDuckGo’s email masking service. By using aliases and unique strong passwords for each new account or platform, your main email account will remain secure in the event of a data breach. This will mitigate a great deal of damage that could occur if you were to use one email and the same password across all sites, which is exactly what hackers take advantage of in credential stuffing attacks.
If you are linking other accounts to your iPhone like Gmail or Yahoo make sure that you have enabled 2FA to ensure that your information stays secure. If you are really looking to take your email privacy and security to the next level we recommend switching to an encrypted provider like Tuta where you get all of these features, plus device side encryption which protects your information locally on the device. That way, should your device find itself compromised by a zero-day attack you can rest assured that the data contained in your Tuta mailbox is fully encrypted and secure.
Directed iOS Spyware (Pegasus)
You may have heard about the Pegasus spyware on the news and it is a truly terrifying piece of spyware. Developed by the NSO Group in 2011, Pegasus is a spyware sold directly to governments for targeted surveillance.
Unfortunately, the company has done less than their due diligence when selling such a dangerous tool and has been sold to governments seeking to crack down on human rights workers and journalists critical of oppressive regimes like Jamal Kashoggi.
Pegasus allows the agency which is attacking your device full access to the data stored on it, the ability to record your screen, access cameras, and use your microphone. What makes this even more threatening is that in 2020 the NSO Group began pushing towards “zero-click” exploits for their software which required no interaction with the victim’s device. There was no need for them to click a link, the message only needed to be delivered and the damage was done.
Apple and Google are actively working against this malware and in 2024 WhatsApp won a lawsuit which will require NSO Group to reveal source code of their dangerous iPhone spyware.
Previously, it was only possible to confirm a Pegasus infection by submitting your iPhone to forensic examination, but recent development by Kaspersky Labs have led to a new possible way of detecting this software by examining the iPhone’s shutdown.log file, but this approach is limited.
Fortunately, using this software is extremely expensive and it is likely that only those who find themselves under threat of direct government surveillance. Apple has introduced Lockdown Mode for users who think this may be an aspect of their threat model.
You can enable Lockdown Mode by following these steps:
- Open your Settings
- Scroll to Privacy & Security
- Click Lockdown Mode
- Tap to toggle on Lockdown Mode for your iPhone
iPhones and the GoFetch Cryptographic Vulnerability
In mid March 2024, a team of researchers made a startling announcement that impacts the owners of Apple’s famous MacBook laptops. The vulnerability, named GoFetch, exploits a hardware design on the Apple M1 and M2 chips (and likely the M3). The flaw allows a malicious piece of software, which does not require any special root privileges, to snoop on cryptographic operations which are being processed on the same CPU cluster. The attack focuses on what is known as a pre-fetcher. A pre-fetcher looks at previously accessed data addresses and then tries to guess the future addresses. The M-series of chips use what is known as a data memory-dependent pre-fetcher, which works a bit different than a classical pre-fetcher.


This puppy might look cute, but when it is leaking your MacBook’s cryptographic keys it’s being a bad dog.
Unfortunately, in their disclosure, the security researchers point out that:
“The DMP then sees that the data value ‘looks like’ an address, and brings the data from this ‘address’ into the cache, which leaks the ‘address.’ We don’t care about the data value being prefetched, but the fact that the intermediate data looked like an address is visible via a cache channel and is sufficient to reveal the secret key over time.”
Because this vulnerability is related to the physical architecture of the MacBook’s processor, there is little users can do to entirely mitigate this risk. What is recommended is keeping up with the regular MacOS updates and installing only verified software on the device to make sure you aren’t accidentally loading up shady programs which seek to exploit GoFetch.
Fortunately, GoFetch specifically targets the M-series processors which are primarily used in Mac computers, but are used in some iPadPro devices. This means, from what we know so far, iPhone’s A-series chips are not affected by this major security flaw. Of course, this research is on-going and we may learn more about possible attacks on the A-series in the coming weeks.
How can you tell if your iPhone has a virus
Although iOS malware is still somewhat rare, there are a few ways of noticing if your device may have been infected.
- New apps or different settings: If you notice new apps which you did not install or settings changes you did not make on the device, this could be signs of malware or that someone has tampered with your device.
- Poor battery life: Some malware or spyware software will run in the background causing your battery to drain faster than it normally would. Please note, iOS devices are known for having reduced battery life over their lifespan, but if a major change occurs with seemingly no reason you might need to restore your device.
- Pop-ups: Pop-ups can occur if you installed a sketchy browser extension and can range from annoying to potentially serious. If you begin encountering unexpected pop-ups you might need to take action to cleanup your device.
- Crashing: Similar to the change in battery life, irregular crashing of your device and apps can be caused by something running in the background and your device might have been infected with malware or been tampered with.
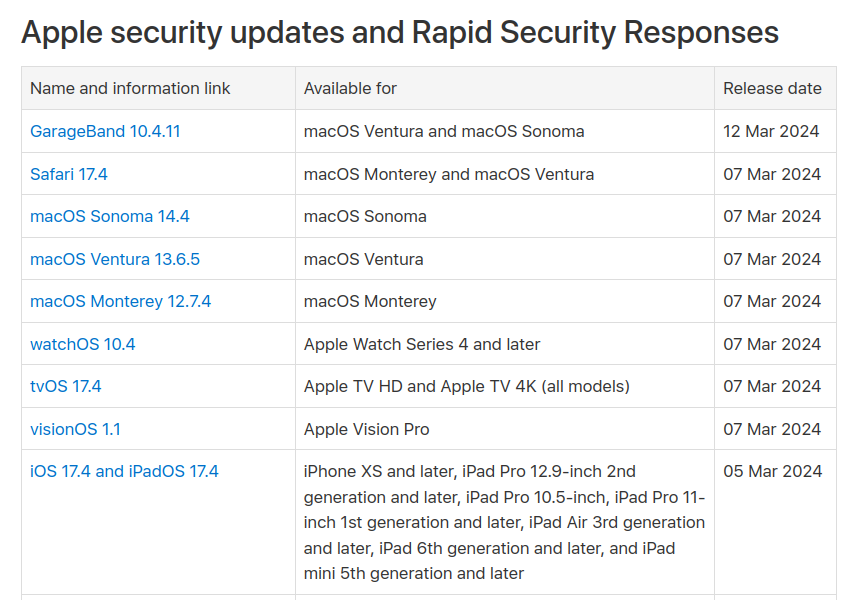

Apple regularly releases new security updates for all devices. Emergency updates will be automatically installed on your device to keep you safe. Chart data made publicly available by Apple.
Tips to remove viruses and restore your iPhone back to health
- Update to latest version of iOS: Apple’s security team is constantly working to improve the security of the iOS ecosystem against viruses and patch vulnerabilities. By keeping your device up-to-date with security updates you are already protecting yourself. Some exploits may be patched and by updating the malware can no longer function as intended.
- Restart Device: Sometimes a simple restart is all you need. If you believe your device has been infected, restarting should be your first step in trouble-shooting.
- Delete suspicious apps: If you find new suspicious apps on your device you should uninstall them immediately. Your iPhone should only be running the software which you intend it to run. This will also remove the data from the questionable app.
- Clear cache and history in browsers: If you stumbled upon a site pushing iPhone viruses, clearing out your browser data will prevent you from visiting this same site again. It can also keep you protected if you visited a phishing site and want to avoid it in the future.
- Restore to Backup or Factory Reset: This is your final option if the device has been hit with malware. If you are using iCloud backup you can rollback your device to a point prior to the virus hitting your iPhone. If this doesn’t do the trick you can also do a full factory reset. This will delete all data from the device and should be considered a last resort before buying a new iPhone.
Apple sets the bar high when it comes to iPhone security
With these tips in mind, you should now feel a bit safer in the measures Apple is taking to secure your device. For most users keeping your device running the latest version of iOS, installing all security updates, and being mindful of your behavior on the device by not clicking on suspicious links will lead to an overall safe smartphone experience. If you are concerned about leaving the app store environment for processing payments we have even introduced an easy-to-use iOS payment system so you can safely fund your subscriptions!
With these practices combined with the use of a password manager you are immensely increasing the security of your digital life. With practical measures to prevent phishing and smishing it is hard to deny that Apple is giving their users easy to use security solutions.
If you are using an iPhone you can make your security even stronger by moving away from a Big Tech email address like Gmail or Outlook and using Tuta’s dedicated iPhone app. With Tuta Mail you will have an end-to-end encrypted mailbox which can be used as the center-point for your digital life. Signup today!
Stay safe and happy encrypting!

