How encryption works
Encryption is not new at all, but the technology powering the ciphering of messages has changed rapidly in recent decades.Ancient Greeks encrypted messages for use in military combat that were sent to commanders by means of a Scytale. This is a tool which wraps a piece of parchment around a wooden rod in order to write or read plaintext messages. Once the parchment is unwound, the message is lost in a sea of unrelated characters, known as ciphertext. By moving the placement of letters this is one example of a transposition cipher.


Today, we have moved beyond classical cryptography which focused upon the order and placement of letters or other linguistic patterns and have turned our attention to mathematical encryption of digital data. Regardless of the leaps in technology, encrypting and decrypting a message always involves a plaintext and a cipher text.
In cryptography, a ciphertext is the jumbled up format of a text that results from encrypting it. Thus, the text becomes unreadable to anyone who does not know the key for decrypting it back into its original form.
Encryption begins with plaintext
When you write down a message, note, or thought on a piece of paper or in your smartphone, the text you are effortlessly reading is what cryptographers call plaintext. This is the data you are creating prior to the application of any encryption measures. Messages in plaintext are not confidential as anyone can read them just as easy as they would read through a newspaper.
The most common place you may hear the word plaintext would be in the context of journalists reporting on data breaches. It happens far to often that hackers find their way into an unprotected system and discover and siphon off a trove of plaintext user data like names, emails, or hashed passwords with or without salt. This means that the data, which may have been stored in a relatively secure network, was itself not protected by means of encryption.
Just remember that whenever we are communicating, regardless of the medium, the initial utterance or text we create is plaintext.
A cipher is introduced…
You might be asking, well, what is it that turns plaintext into ciphertext? The answer is a bit on the nose, a cipher is what causes this state change. A cipher is defined as a cryptographic algorithm which converts letters or bits of data into ciphertext.
There are many famous examples of ciphers, some of which you might already know!
-
Caesar Cipher: This famous cipher rearranges the order of letters by off-setting them. Our plaintext “Howdy” could become ciphertext “Jqyfa”. In this case the cipher is replacing each letter with the second one following it.
-
AES: the Advanced Encryption Standard is a block cipher used in ATM machines, email, and remote access software.
Ciphertext is ready for transfer and future decryption
Once a message or piece of data has had a cipher algorithm applied to it, it is considered encrypted. Depending on the strength of the cipher being used, the data will be more or less vulnerable to interception and decryption. Some algorithms are “one-way” ciphers which are used for hashing or creating checksums, these are not intended to be decrypted.
Currently, AES256 is considered a quantum-safe encryption algorithm (cipher) for data at rest. This means AES256 can keep your secrets safe much better than simply jumbling the contents of an important letter with a Caesar cipher.
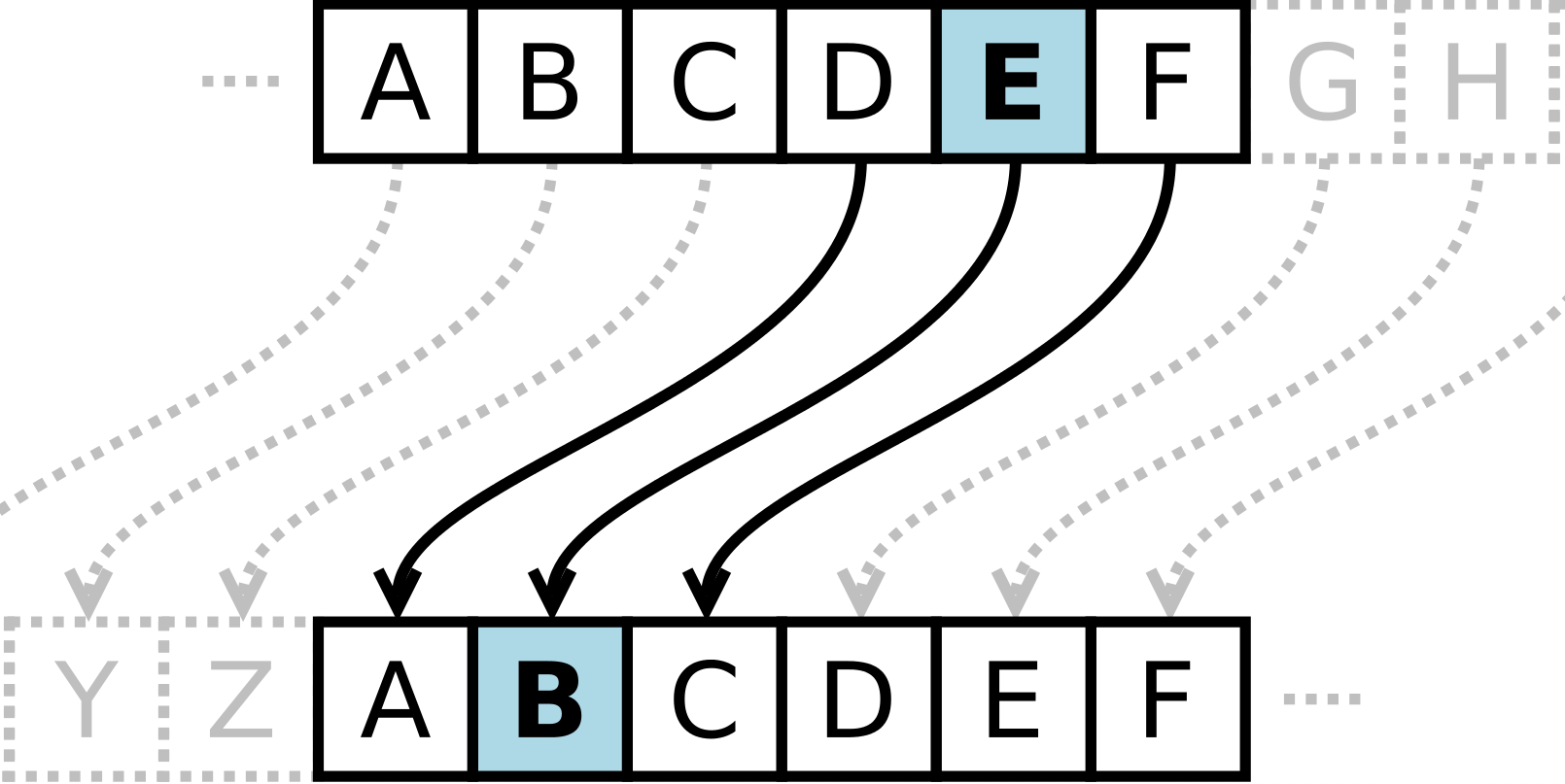

Knowledge of the cipher being used to encrypt a plaintext, and the keys used in the process are crucial for the recipient being able to decrypt and read your message. In the case of our Caesar cipher above, the recipient would be able to quickly “decrypt” our message if they know we are using a Caeser cipher with a 2 “key”. They will know to roll back two letters to uncover and read our plaintext message.
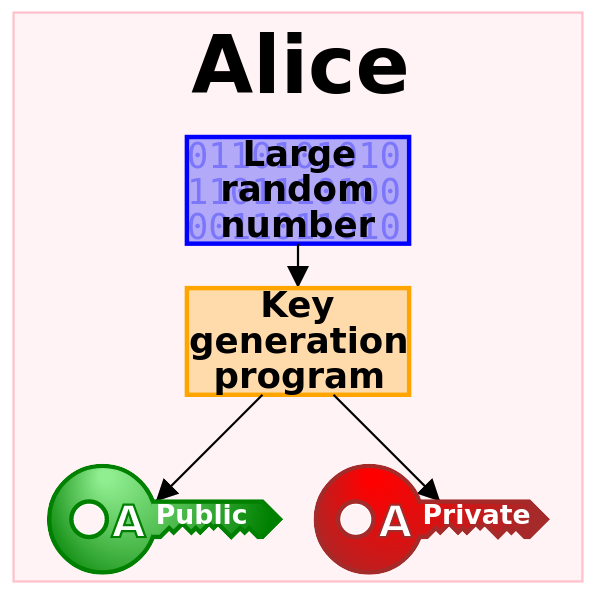
More complex encryption algorithms operate in a similar manner but the means of key exchange are more complicated. In order to decrypt a symmetrically encrypted piece of data, we will need to know the singular encryption key. If our sender used asymmetric encryption instead, they will need to have previously accessed our public key to encrypt the message and we will use our private key to decrypt it. We show this in more detail in our explanation on cryptography basics.

Asymmetric public key encryption is used for modern emails to securely exchange messages.
Plaintext + cipher = ciphertext
To recap, most encryption follows the similar path of plaintext + cipher = ciphertext. In turn, when it comes time to read the encrypted message by the recipient, the formula is inverted ciphertext – cipher = plaintext.
Now you know some of the basic terminology which sits beneath encrypted communication.
Types of ciphers
Modern ciphers are more complex than what the Ancient Greeks or Romans used, but they work very similarly. Modern ciphers differ by how they handle keys:
Symmetric-key ciphers
In symmetric encryption one single key encrypts and decrypts the data. This cipher is also called private-key cipher. The best known symmetric-key cipher is AES.
Asymmetric-key ciphers
Asymmetric encryption uses a pair of key - a public key and a private key to encrypt messages from one person to another, for example when you exchange encrypted emails or encrypted chat messages. These are also called public-key ciphers, the most prominent one is the asymmetric encryption with a combination of AES and RSA algorithms.
Where are ciphers used?
Ciphers are all around us. They are using in the chips in your credit card, mobile phone calls, connections to a WiFi access point, or even sending silly secret codes to your friends.
Encrypted services like Tuta are one place where you can find AES and Eliptic Curve Cryptography being used to encrypt your emails, calendar events, and contact info!
Your web browser is using a cipher right now to reach this website via TLS!
Email encryption
Big Tech companies like Google, Outlook and Yahoo! all use encryption ciphers to protect your data from prying eyes.
-
These email providers rely on TLS for securing your emails in transit,
-
and on symmetric-key encryption (mostly with AES256) to encrypt your data at rest when stored on their servers.
While both encryption ciphers work well to protect your data, these services also hold the key for decrypting your data so that it is not protected from third-party access.
Tuta Mail on the other hand offers quantum-safe end-to-end encryption for your data when stored in your mailbox and while it is in transit. While other encrypted email providers might protect your messages with end-to-end encryption, they too need to improve their ciphers because right now they cannot protect from the threat of quantum computers. In addition, Tuta Mail lets you send password-protected emails to anyone in the world and uses a zero-knowledge architecture to make sure that not even we at Tuta can access your encrypted data.
Security you can trust
Modern cryptography is not built on clever means of shuffling letters, but on complex mathematics. Today’s encryption algorithms give us a mathematical guarantee of complexity and security which meets even the most extreme threat model. While the quantum-resistant encryption algorithms are rather new, they are also published as open source so that they are rigorously screened for weaknesses by cryptanalysts around the world who are committed to creating strong, reliable encryption.
At Tuta, we work directly with research cryptographers both in-house and with partners from universities. We are building quantum-safe encryption that you can trust.
Take back your privacy today by signing up for encrypted email!

