Understanding Cryptography: The Basics
The Differences Between Asymmetric and Symmetric Encryption
Symmetric vs Asymmetric Encryption: What is the difference?
Cryptography is the study and practice of achieving secure communication that needs protection from an adversary. Cryptosystems can utilize complicated mathematics or be as simple as the language game “Pig Latin” which regularly appears on school playgrounds. The use of cryptography is to keep what you wish to say safe from nosy eavesdroppers. Of course, the different types of encryption that we use on a daily basis for online banking, hashing passwords for secure storage on websites, when using ATM cards, verifying checksums, and in our smartphones is built on a number of mathematical algorithms which are engineered to keep your digital data safe. Of these algorithms, there are two primary forms: symmetric encryption and asymmetric encryption. The common notion of what people think of when hearing about spies and secret codes is an example of symmetric encryption, but in truth there is much more complexity when it comes to securing your communications. So what are the differences between symmetric and asymmetric encryption? Let’s find out.
Symmetric-Key Encryption
Symmetric Key Cryptography earns this name because it employs the same secret or key, in order to encrypt and decrypt data. There are different forms of symmetric ciphers, but if the encryption and decryption key are identical, then they fit into this group.
We’ve collected even more information on what is a ciphertext in another cryptography basic post.
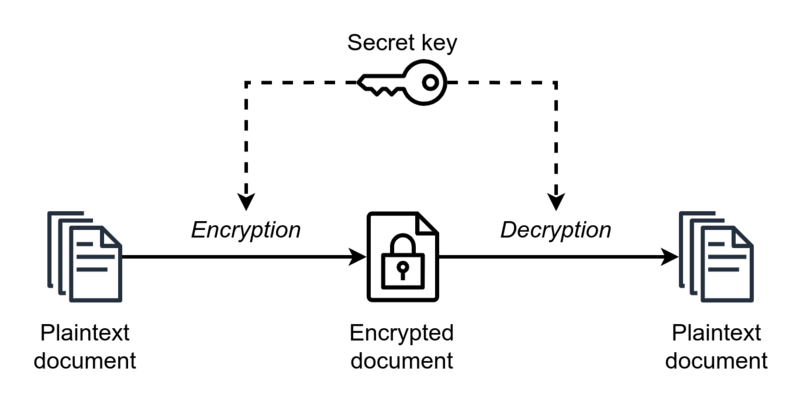

In this example we see Alice using the same key to encrypt the document as Bob uses to decrypt the document.
Not all encryption algorithms function the same way, and symmetric encryption comes in two major flavors that of the stream cipher and the block cipher. The main difference between the two comes down to how the bits of data are encrypted. A stream cipher will encrypt all the bytes of data one by one individually by combining them with a pseudorandom number generated by a keystream (hence the name) until the entirety of the data has been encrypted. Block ciphers on the other hand will group an unvarying number bytes together and encrypt the groups. Should the final group be of a smaller size than the other blocks, that group will be “padded” so that it reaches the corresponding block size. Stream ciphers tend to be faster than a block cipher and can also run on less powerful hardware, but they are more prone to security risks.
Well-known Examples of Symmetric-Key Cryptography
Probably the best known symmetric-key algorithm is Rijnael/AES. AES (Advanced Encryption Standard) is a block cipher which became the default symmetric encryption protocol as a replacement for DES. After winning NIST’s competition for the DES successor AES quickly became an industry standard. Today, AES256 (AES with a 256-bit key) is considered to be quantum resistant by cryptographers and security experts.
_Round_Function.CaY6mPFq_Z1XnRnN.png)
_Round_Function.CaY6mPFq_Z1XnRnN.png)
An example of the round function in AES.
When is symmetric encryption used?
Symmetric encryption is generally used for encrypting bulk amounts of data due to its speed. For example, in Tuta all user data is encrypted on the client-side using symmetric encryption with AES256. You likely use symmetric encryption around your house if you are using a WiFi connection as WPA builds upon symmetric cryptosystems. Symmetric encryption runs into difficulties when communicating with other parties because there must be a secured way of sharing the encryption key. That is where asymmetric-key encryption comes into play.
Asymmetric or Public Key Encryption
Asymmetric-key exchange first came into public view in 1976, following the publication of a ground-breaking paper by Whitfield Diffie and Martin Hellman. Also termed “public-key” cryptography asymmetric encryption used two keys instead of a single shared key. In the public-key encryption model, a public key can be used to encrypt a message and the recipient’s private key will be used to decrypt it. Asymmetric-key encryption is particularly useful for communicating over the internet, as the public key is designed to be public and must not be protected in the same what that a symmetric encryption key should be.
Popular Examples of Asymmetric-Key Cryptography
Many of the more well known cryptographic algorithms reside in this category. The RSA cryptosystem, SSH and TLS/SSL protocols, and the program PGP are all popular examples of asymmetric cryptography. RSA has been an industry standard, but has recently fallen out of favor with the pursuit of creating quantum resistant encryption.
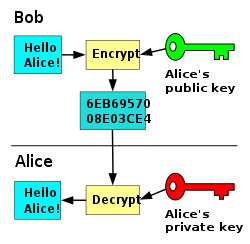

This graphic shows how Alice and Bob use private and public keypairs for encrypting and decrypting data.
When is asymmetric encryption used?
Asymmetric encryption is primarily used for sending encryption keys across the internet. If the content of your message has been encrypted using symmetric encryption, then you will need to securely share the secret with your message’s recipient. This is done with asymmetric encryption. Public-key cryptography is slower than symmetric cryptography and for this reason also tends to require more resources to encrypt and decrypt data. There is a higher degree of security due to using different kinds of keys (public and private) in combination to meet a higher security requirement and because the size of the keys is typically not too large (in comparison to large documents, images, or video) it can be used to securely transmit the symmetric key for decrypting the larger body of data.
This hybrid cryptosystem is often used in messaging applications which will use a symmetric key to encrypt the body of data, and asymmetric encryption for sharing the secret required for decrypting and accessing the encrypted data.
Cryptography is the key to online privacy and security
Cryptography is a massive field, rich in mathematical depth and complexity. Proper deployment of cryptographic protocols is a cornerstone of protecting your data and online privacy. There is no requirement that you understand the intricacies of encryption in order to start taking back your privacy. Tuta makes using encryption fast and simple.
With a few easy clicks you can begin employing our strong post-quantum encryption to take back your right to privacy.
Signup for a secure Tuta account today!
Find out more about the encryption algorithms used in Tuta and check out our detailed encryption page.

