Zero-Knowledge Architecture and Your Data
An introduction into how Tuta combines zero-knowledge infrastructure with post-quantum encryption for maximum privacy and security.
What is Zero-Knowledge Architecture?
There is lots of talk about privacy within the tech industry but not all companies offer true privacy. If you are shopping around for a new privacy respecting digital home, you need to make sure that any candidates are using zero-knowledge architecture so that only you have access to your data. Companies like Google and Apple claim to protect your privacy, but if anyone in addition to you has access to your encryption keys, your data is not completely secure. At Tuta, we have no access to data stored inside your account because we have no access to your encryption keys.
Zero-knowledge services, also commonly referred to as no-knowledge or zero access, are online platforms which encrypt data in such a way that it guarantees a high degree of confidentiality. Confidentiality means taking security measures which make sure your data is only available to authorized persons (you and anyone else you allow). We have previously discussed the importance of confidentiality in our threat modeling guide as part of the CIA Triad. By encrypting your data on your device in Tuta Mail, we never see the contents of your communications or the subject lines of your messages when using our post-quantum end-to-end encryption.
Client-Side encryption is crucial to true security.
At Tuta, when drafting and sending an end-to-end encrypted email, it is always encrypted on your device before reaching our servers and being sent across the internet. This minimizes the damage possible by a man-in-the-middle attack as all they could possibly gather would be encrypted data which is nonsensical.
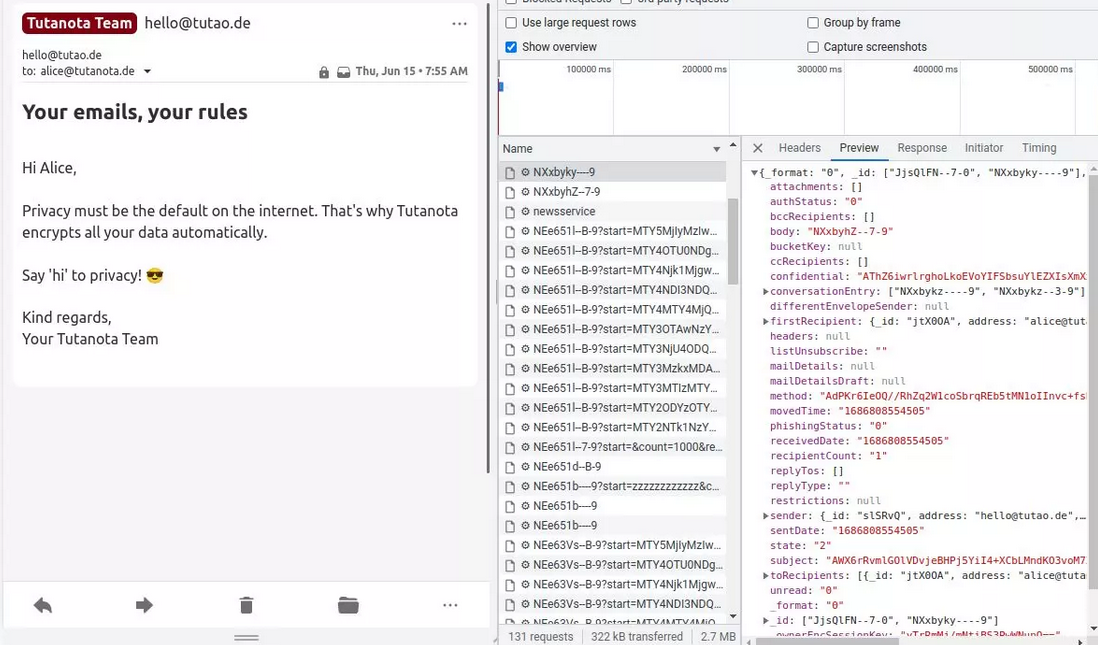

An example of how Tuta Mail encrypts all data in the mail client before sending.
Tuta uses your password on the client to encrypt your encryption key, which then encrypts all your data. As the entire encryption process is handled locally on your device, we never see any of your decrypted data. Tuta has zero access to any unencrypted data that might be stored in your emails, calendars or contacts.
All cloud-based services store data on their servers. This is a simple fact, and if this is a major hurdle for your threat model then self-hosting will be the only true solution for your needs. However, self-hosting does not come risk-free and choosing a service dedicated to your security and privacy like Tuta could be the safer option as the whole focus of the Tuta team is to keep your data secure. Tuta’s automatic encryption makes sure that your data belongs to you – and to you alone. This level of privacy is a step beyond other service providers that have full access to your data. Not only does zero knowledge architecture protect you, but it also protects those who you care about as well. By sticking with services committed to using zero access configurations, you are doing your part in making the internet a safer place for everyone.
Zero-knowledge architecture goes beyond email
The end-to-end encrypted service Tuta make sure that your data can not be exploited with their zero-knowledge architecture. What sets Tuta apart from other encrypted service providers is that we encrypt more metadata as well. This includes your entire contacts’ data and calendar events, including event notifications which are also zero-knowledge. Not only do the Tuta servers not see what events you are scheduling, but we cannot see when they are being scheduled either.
Another outstanding feature in Tuta Mail for protecting your privacy is by having deployed our own push notification service instead of using Google’s FCM for sending email notifications to your Android device. By taking these extra steps, our servers never see the notification, and neither does Google.
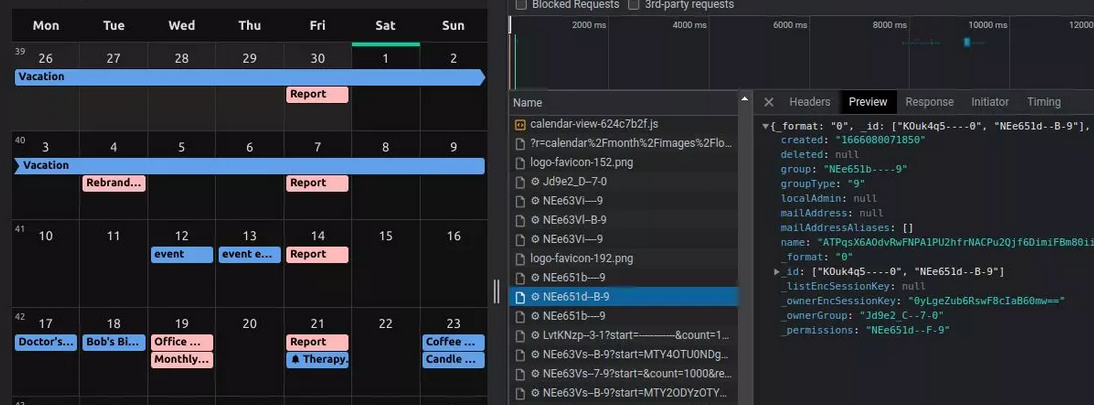

An example of the encrypted calendar meta data that sets Tuta apart from other encrypted service providers.
The same high degree of confidentiality is also applied to your Tuta Contacts. We automatically encrypt all the available data entry fields for each individual contact, even email addresses. This prevents us as a service provider from ever having access to any personally identifiable information of those you are in contact with.
This is privacy done right.
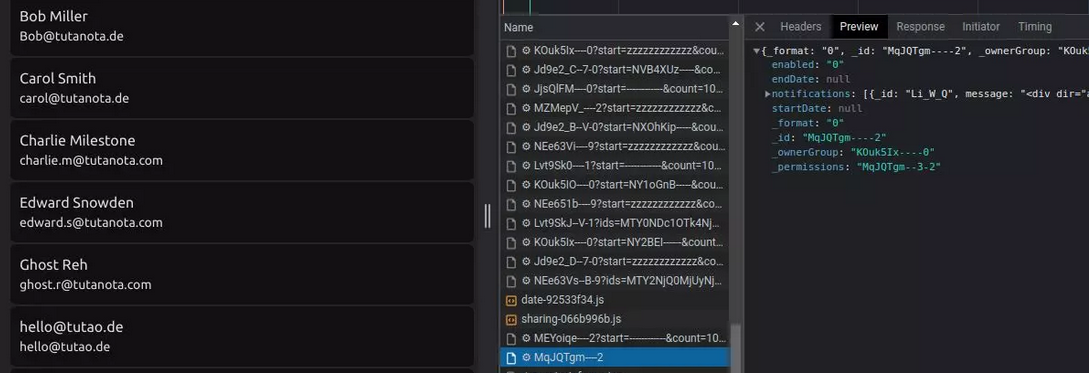

An example of how Tuta has introduced zero-knowledge architecture to our Contacts feature.
Why zero-knowledge infrastructure is a no brainer!
If you are concerned about your privacy, it is important to choose services that really put privacy first. Without a verifiable guarantee of zero-knowledge architecture you cannot be sure that your data is truly secure. This is why we publish all our client code fully open source. This means privacy and security experts around the world can confirm that Tuta really is providing the strongest and most comprehensive encryption available for your emails, calendar events and contact information.
Privacy and anonymity are crucial for free speech. Our zero access infrastructure allows you to create email accounts, both free and paid, in complete anonymity. This along with the end-to-end encryption is a necessity for whistleblowers, activists, and journalists whose physical safety may be at risk by speaking truth to power. Tuta is built with this kind of threat model in mind, that’s why we have made an easy to follow guide on our YouTube channel for creating anonymous accounts while using the Tor network.
We’re building privacy that you can trust.
When it comes to protecting your data, regardless of your threat model, don’t settle for less. Tuta Mail encrypts more data than other encrypted service providers and is the world’s only quantum-safe solution for email.
Turn on privacy by creating your Tuta account today!



