What is a checksum? Cryptography Basics
An introduction to cryptographic checksums, their usage, & how they keep you safe.
What is a Checksum?
A checksum is a string of data, both letters and numbers, that is derived from a file or program through a checksum hashing function, and is used to verify that the data you have downloaded is identical to the original source data. Ensuring the integrity of the files and programs you are downloading to your local machine is a crucial security practice to keep yourself safe from fake programs being shared which include malware for harvesting your data.
Remember it is always a best practice to verify the checksum of files and applications you download whenever possible.
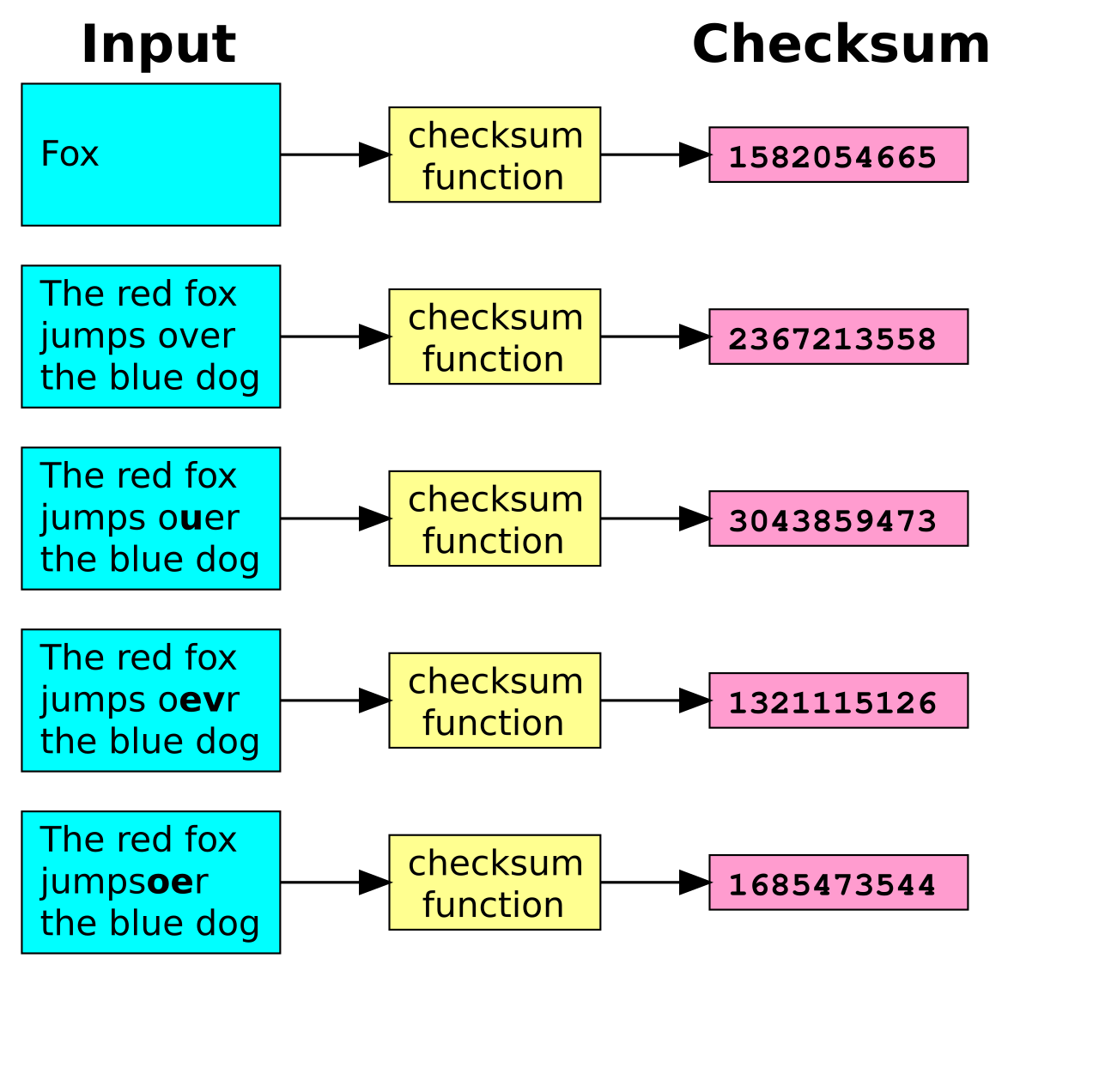
An important feature of a checksum function is that if any changes are made to the original file, these will result in a different output, e.g. a different checksum. Without this key feature, a malicious actor could make changes to the data through a man-in-the-middle attack or a supply-chain attack and users would be none the wiser.
Checksums also need to ensure that not only changes in data lead to a new key, they must avoid the possibility of two different data sources creating matching checksums. These events are known as collisions and the strength of a cryptographic hashing function relies on being collision resistant.
Checksums ensure the integrity of your data, not authenticity.
Checksums are primarily used for verifying the integrity of data. You might remember from our introduction to threat modeling, that integrity refers to the data having been transferred to your machine in a digitally identical format. This means that you are receiving the data, be it a file or executable program, as intended by the content creator. One point of note is that checksums only verify that the data you received is 100% identical, it does not verify that the source itself is authentic. This is another aspect of information security which can be achieved through the deployment of a digital signature.
Why is data integrity important?
Data integrity is paramount across all levels of IT operations. From enterprise data storage, emergency services, public sector services, to pictures of food from your last vacation. Data corruption, the opposite of data integrity, can lead to program errors or important information going missing. By maintaining checksums, you can rest assured that data you might be copying, downloading, or sharing is identical without needing to open and manually review it.
If you can’t trust your data its use decreases greatly. By taking advantage of checksums, you can be sure that an error you might encounter with that new program has another source and isn’t due to things going awry during the initial download. This can save both time and money. If you are maintaining backups of your data, creating and monitoring checksums of these backups is a great way of keeping an eye on the status of all data being stored. Should you notice a difference, without having made any changes, you can be alerted so something going awry.
What causes non-identical checksums?
There are a number of issues that can lead to checksums not matching, both mundane and malicious. An interruption in internet connectivity or issues with storage space can be the cause of missing data which will then result in a checksum which fails to match those provided by the original course. Once resolved, a fresh download typically returns the correct value.
However, there are malicious cases which might be cause for alarm. Mismatched checksums could also be an indication that some third-party has made changes to the original source data. This might be something minor, but it could be the sign that malware could have been included in the download. This becomes even more of an issue when the programs in question will be used for sensitive data like the storage of passwords or cryptocurrency. Repackaged malicious password “managers” can send your data directly to third-parties where it can be abused. In the case of impostor cryptocurrency wallets, the fallout of mismatched checksums could result in a complete loss of digital assets.
Examples of algorithms used for generating checksums.
Regardless of which hashing algorithm is being used to create the checksum, they all have in common that they are one-way functions. The value generated by the checksum function cannot be used in any way to “recreate” the original file. This isn’t encryption and there is nothing to be decrypted, so we are not dealing with cipher texts.

Some of these algorithms might look familiar and we have previously discussed some of them in previous entries in this Cryptography Basics series.
MD5
Just like with hashing passwords, MD5 should no longer be used because it can lead to collisions which means that a malicious actor could create a fake version of the software you are wishing to download and a checksum would fail to raise alarms to these changes.
SHA-1
This hashing function hasn’t been considered secure since 2005 and NIST has called for it to be completely retired by 2030. In 2017, Google along with the Cryptology Group from the Centrum Wiskunde & Informatica were able to create two different PDFs which resulted with the same SHA-1 fingerprint.
SHA256
The current standard for checksum hashing is SHA256 (or SHA-3 for fans of the new). SHA256 is also the checksum function we are using so that you can check the integrity of the data every time you download the Tuta Desktop Client.
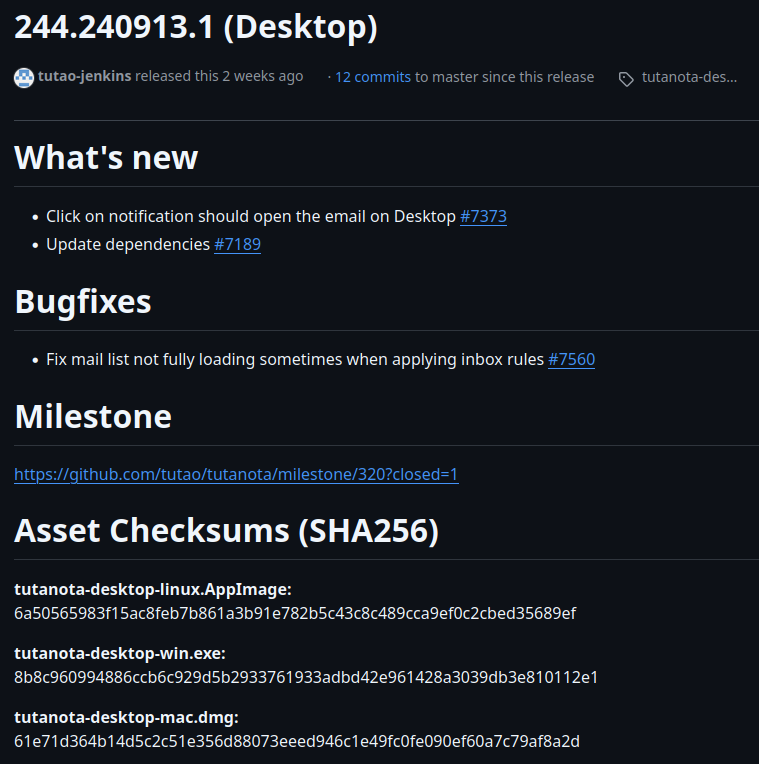

How to verify the checksum of your Tuta Desktop Client.
Verifying the checksum of a download might appear to be a daunting task for those who may not feel very technically inclined, but it is a quick skill to learn that can save you lots of headache down the road.
With every new release of the Tuta desktop client we publish the checksums on Github so that you can verify them, regardless of your device’s operating system. The first step will be to visit our homepage and download the desktop client which matches your operating system. Go ahead, I can wait…
Great! You’re back! Now you can skip to whichever OS you are currently using and with a few simple steps you can verify the checksums of your download. For simplicity, I will be writing these instructions under the assumption that you stored the download in your Downloads folder.
Windows
On Windows, please open the command prompt from either the start menu or by running cmd in the Run dialog window. Now that you have the command prompt open type:
-
cd Downloads
-
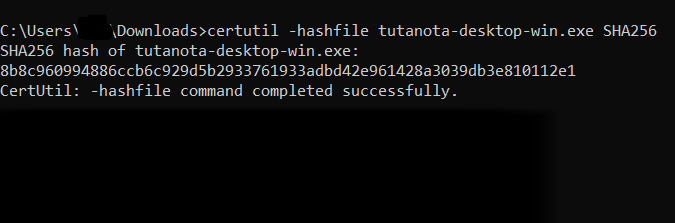
certutil -hashfile tutanota-desktop-win.exe SHA256
This output can be compared to the checksum we provide on GitHub.

You can download the Windows client here.
Mac
On a Mac you can open a terminal window from the Launchpad. Once it is opened please enter the following:
-
cd Downloads
-
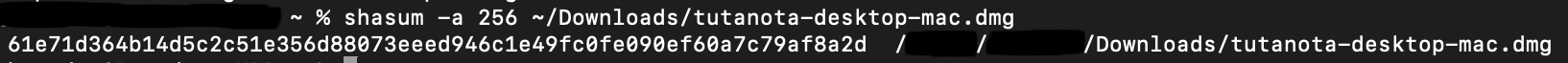
shasum -a 256 ~/Downloads/tutanota-desktop-mac.dmg
This output can then be compared to the checksum provided on GitHub.

You can download the Mac client here.
Linux
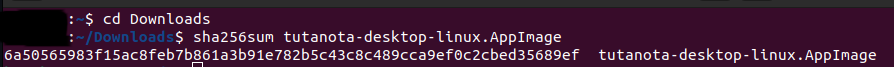
Last, but certainly not the least, you can verify the checksum of our free Linux desktop client by opening a terminal and entering:
-
cd Downloads
-
sha256sum tutanota-desktop-linux.AppImage
You can then compare this output to the checksum provided by the development team at Tuta to confirm the integrity of your download.

You can download the Linux client here.
With this new security trick up your sleeve you can continue your journey of staying safe on the web. By including the verification of checksums into your digital hygiene, along with using a password manager you are taking action to protect yourself from cyberthreats.
If you are looking to improve the security of your email account, and we recommend you do because email is the hub of your digital life, check out Tuta Mail. With default end-to-end encryption, Tuta Mail makes privacy and security simple. Create your free email account now and use it with our free dedicated email clients for all platforms.
And don’t forget to verify the checksum! 😉

