How to tell if your accounts have been hacked: Your ultimate guide for 2024
With a never-ending wave of data breaches leaking user login information, it's time to learn all the ways you can tell if your accounts have been hacked.
Signs of a hacked account
With the troves of user information available due to the unstoppable flow of breach data, credential stuffing attacks are on the rise. A malicious account takeover can happen fast, but by noticing the signs of a potential attack, you can prevent malicious actors from gaining control of your accounts and locking you out. Not only does this protect your account data and personal information, but by keeping a watchful eye on your accounts you can help reduce the amount of spam. Additionally, slow the spread of other types of phishing attacks which might try and takeover the accounts of those listed in your contacts or friends lists.
There are some telltale signs that your account might have been compromised, and these can vary based upon which platforms you are using. First, you might get an initial hint that your account has become a target if you start receiving password reset emails or push notifications related to new logins from your favorite social media apps or email provider. These can be attempts by bots who have discovered your public facing accounts which then try to reset your password. Before clicking any links in the email, it is crucial that you verify that it isn’t a phishing attempt. Requests to enter your login information to verify account ownership can be clever ways for attackers to trick you into turning over your login information.
If you are concerned that your data might have been included in a breach, and for most folks this is sadly the case, you can utilize resources like Have I Been Pwned to determine where your information has been exposed.
Maybe you try and open your social media apps and you are mysteriously logged out. Entering your password might get you back in, but this can still be a sign that someone managed to get into your account and they ended your session but did not reset your password. If you are suspicious, you can always check the open sessions and connected devices in your account settings menus.
There may not be any actively connected devices, but it is also important to regularly check to see if any unknown automatic forwarding or [IMAP/POP connections are enabled. This is especially important as it could be an indicator that someone is snooping through your emails. This might be the case if a hacker is looking to steal account information like login information for your online banking accounts.
Let’s dive into how we can review the connected devices in our email and social media accounts to detect signs of compromise within your accounts before it’s too late.
How to check connected devices in Gmail
Your email account is the hub of your digital life. It has become a mandatory piece of contact information when signing up for any online services or apps, opening a bank account, or when visiting a doctor. Because of this central role, your email account is an enticing target for hackers or other malicious actors looking to steal your personal information or hijack your account for use in spamming campaigns. With Google’s Gmail (even though there are better alternatives like Tuta Mail) being one of the largest free email services in the world, Gmail accounts are a prime target for attack.
There are some telltale signs that your account has become of interest to persons with unseemly intentions that you can watch out for. This first, as mentioned above is to check your account for irregular activity, like finding strange emails in your Sent folder or unknown devices connected to your account that you find in Session Handling. To check which devices currently have access to your Gmail account, you can check under the following:
- Click on Settings > Security
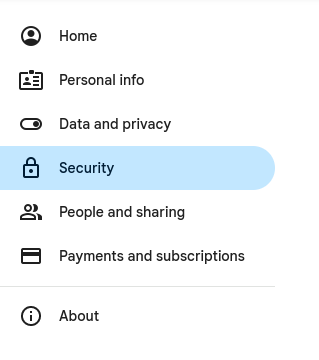

- Under Your Devices you can see all devices which are currently connected to your account.
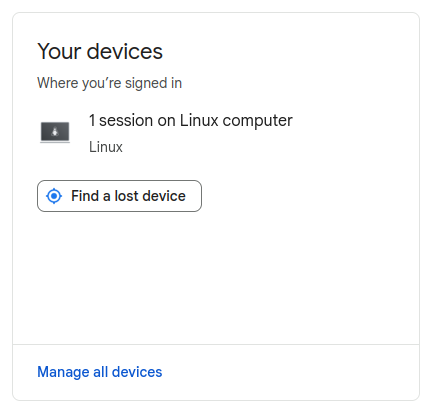

- To view and remove unknown devices from your Gmail account you can click on Manage all devices which will then allow you to remove any devices you don’t want to have access to your account and your data.
One point worth noting is that if you switch devices, like when you purchase a new phone, and forget to end the session that device will still be listed there. So if there is an older device model listed here which you owned previously, this may not need be cause for concern. Out of security concerns, it is advisable to remove devices which are no longer in use.
How to manage devices in your Outlook account
Outlook (for which there are also better replacements), like Gmail is another major email provider with over 500 million active users. Outlook is also a dominating presence within the world of enterprise IT. Like Google’s Gmail, Microsoft’s Outlook provides a number of security features to keep your account safe like multi-factor authentication and passkey support. You can also view which accounts are connected and remove any that might not belong to you.
-
By clicking on your account icon and then choosing My Microsoft Account. You will then be redirected to the account overview page.
-
Click on Devices.
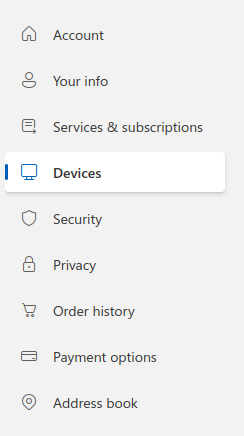

- Here you can now view which devices are linked to your account and remove any that you do not trust or wish to have linked.

If you are longtime user of Outlook (or even Hotmail), keeping an eye on this menu can alert you of the snooping eyes of a malicious actor. This is especially important if you are utilizing Outlook’s web mail service for your business. Account security mistakes pose the risk of data breach, revenue loss, and a tarnished reputation.
Keep your messages secure
Attempts to takeover WhatsApp accounts for gathering contact lists and sending spam are on the rise as well. To protect your WhatsApp account from getting hacked it is of course highly recommended that you enable multi-factor authentication. This is available in the form of a PIN code which can be manually required in the app or sent via email. By enabling this feature you are keeping your WhatsApp conversations safe from anyone seeking to gain access to your account.
You can also monitor the devices which might have been linked to your account. You can do this by following these steps:
-
Open WhatsApp on your device.
-
If you are using an iPhone click on Settings. If you are using an Android device click the three vertical dots.
-
From here on either system choose Linked Devices.
-
Within this window you will see a list of all devices linked to your WhatsApp account. By tapping devices you can log them out of the account.
Should you discover any unknown devices, you should immediately remove them and make sure you have enabled push notifications and multi-factor authentication. This will provide you with a notification message should anyone try to log back into the account, which you can then deny. To stay safe on WhatsApp it is also recommended that you do not login to the account through unofficial versions of the app.
Signal
Signal’s post-quantum end-to-end encryption can only protect your data if you keep intruders out of your account. Just like WhatsApp, you should make sure to have created a PIN to protect your account from being taken over. These PIN codes can be enabled within the settings menu of your Signal app.
To check for any unapproved desktop or tablet devices which might be linked to your account you can follow these steps:
-
Open Signal and click on Signal Settings beneath your user profile picture.
-
Choose Linked Devices.
-
Here you can both add and remove devices.
At present, Signal does not support multiple mobile device logins which means that if you are migrating to a new device, you cannot have both logged in simultaneously.
Was my Facebook account compromised?
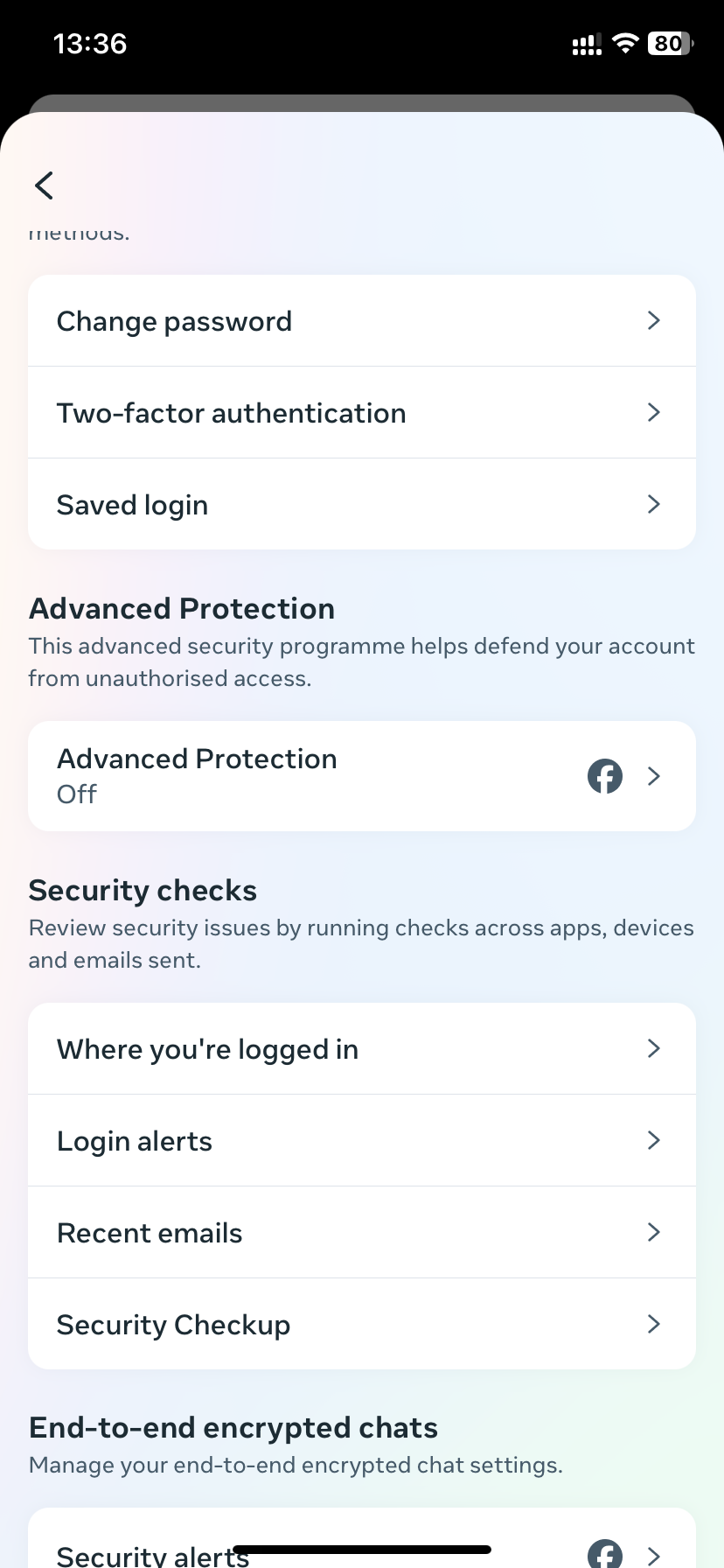
Facebook has become a mainstay for not only social media interactions, but also for use with services like Messenger and Facebook Marketplace. Facebook Marketplace in particular poses a unique target for hackers looking to create reliable looking accounts for use in scam campaigns. To review which devices have access to your account, and determine if your Facebook has been hacked, you can follow these steps:
-
Open your settings and click on Accounts Center.
-
Click on Password and security.
-
By choosing Where you’re logged in you can see all sessions where you are currently logged into Facebook. If any unknown devices are listed here you can remove them and should then immediately change your password and enable two-factor authentication.

While you’re in this settings menu, you can also take some time to check the overall privacy settings of your account and take any additional steps which might improve your privacy on Facebook.
How can I know if my Instagram has hacked?
Another mainstay Meta product, Instagram includes similar steps for managing account access. Checking every so often to make sure nobody has snuck their way into your account which could grant them access to your private images, friend’s information, and any DMs which may be in the account. Meta’s security steps for reviewing this information also includes a follow-up option which will help you reset your password should any unauthorized activity be detected.

Securing your LinkedIn
While searching for the latest job has become a primarily online activity, so to have internet users become accustomed to providing networking websites like LinkedIn or Indeed with the personal data contained in their CV. With the rising amount of fraud and attempted identity theft via LinkedIn, it is crucial that you regularly check to make sure that your account is still secure.
- Open the Settings menu and choose Sign in & security.

- Click on Where you’re signed in and review/remove any unknown devices. This will cover any devices which are actively logged into the account, so afterward you should also check under Devices that remember your password.
Due to LinkedIn’s emphasis on job hiring which requires official documentation, users are more likely to overshare information. When filling in your profile always keep in mind to only include the minimum required data. Data like your email address or birthday are not required for the initial stages of hiring, if a field requires some entry you can always include “Available upon request”.
If your main concern is your personal security and privacy, you should also consider getting off of LinkedIn as the Microsoft-owned company uses your data for AI training purposes.
Keeping your Twitter/X account secure by managing connections
Twitter/X is known for the prevalence of bot accounts, with reports from CNET in 2017 claiming that nearly 48 million accounts were operated by bots. One way of keeping your account safe from getting hacked and the wave of spammy bots is by regularly monitoring what devices have access to your account.
- To check this click on the Settings menu.
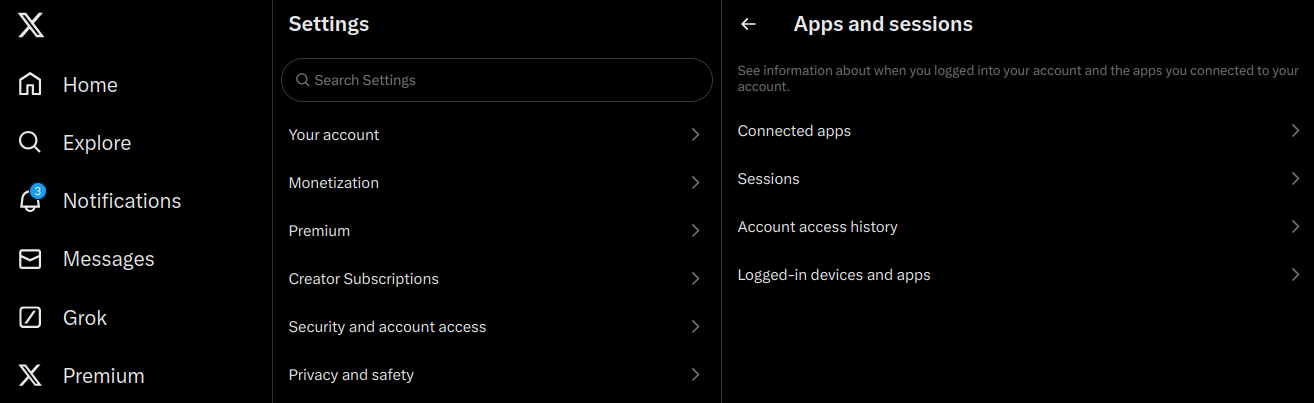

- Then choose Security and account access.
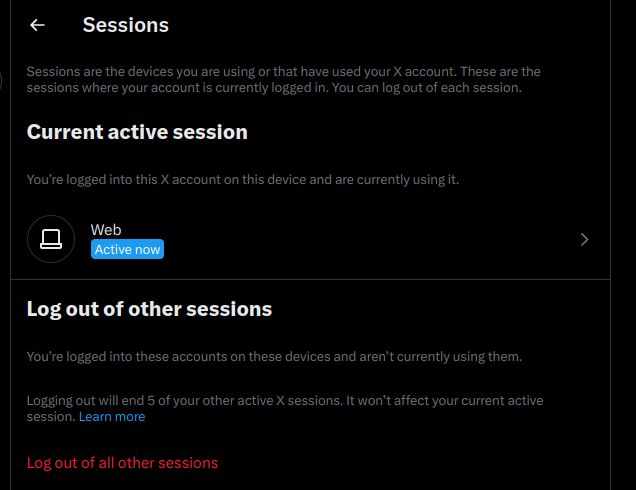

- Within this menu you can view third party apps which might be linked to the account, currently open sessions, devices and historical access information.
As with all other platforms we have discussed, should any unknowns popup during your review immediately change your password to a randomized secure password and enable second-factor authentication. One nice feature available to Twitter/X users is the ability to add a physical hardware key to your account like a Nitrokey.
Lock down your TikTok account
Despite trailing behind Facebook and Instagram in total number of users, TikTok is the most popular social media app for the next generation of internet users. Proving to be a massive social and economic force, TikTok accounts are also useful for scammers looking to create fake accounts for sending spam or promoting content.
To check if your TikTok account has been accessed by a scammer you can open your app and click the three horizontal lines in the top right corner to open the initial settings menu.
- Choose Settings and privacy.
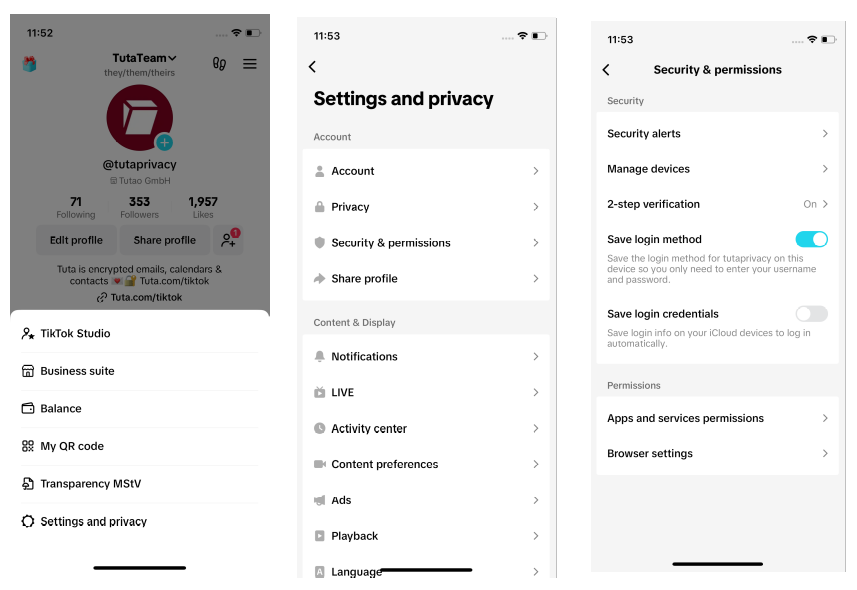

-
Click Security and permission.
-
Here you can review the connections by choosing Manage devices.
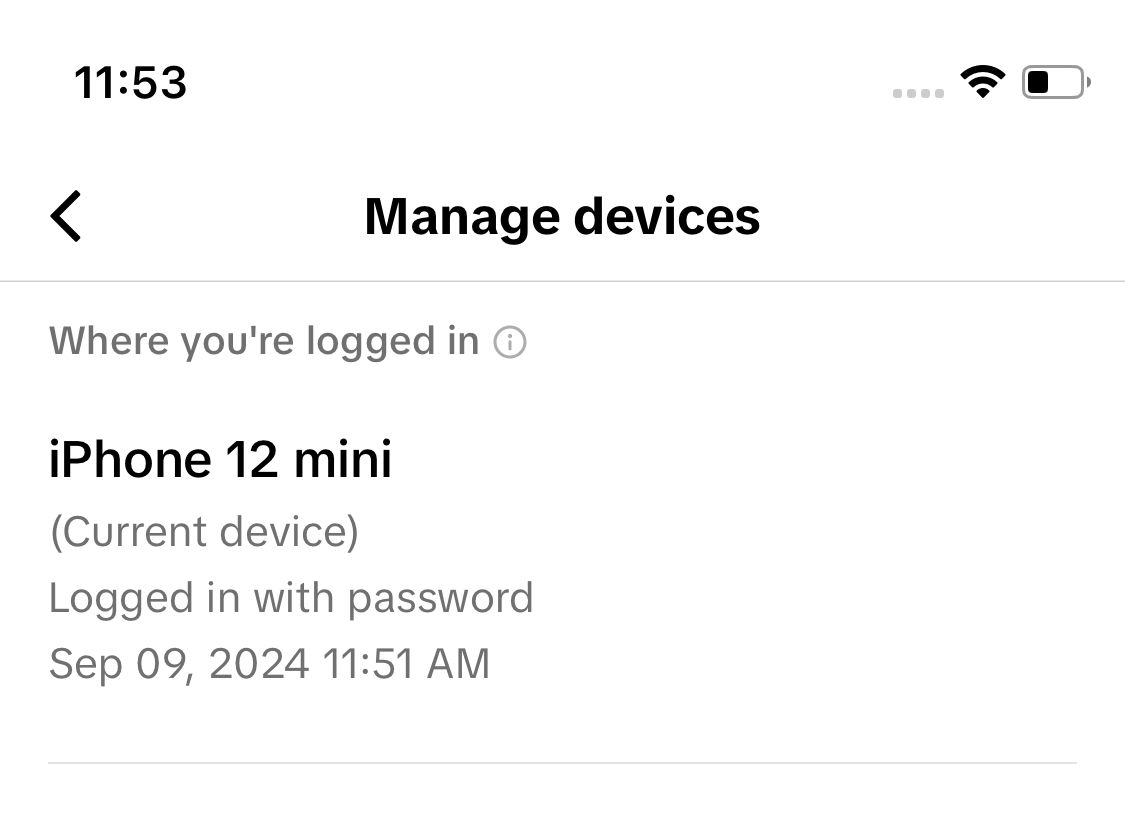

Just like other apps, should you discover a squatter in your account you can give them the boot, change your password, and enable 2-step verification in the form of a verification code. At this time the only options available are SMS (not recommended), a security code via email, or a TOTP authentication code. Of these options, we would recommend the authenticator app as a priority choice. Unfortunately, U2F is not available, but maybe support for physical hardware keys will get introduced in the future (fingers crossed).
Tuta: Secure Email and Calendar with easy device management.
Just like other email and social media platforms, Tuta Mail allows you to easily check where you are currently signed in, and also provides a login history which will show you any previously closed sessions. This allows you to keep tabs on what is happening in your account. Should an unknown device be listed here, you can quickly remove it.
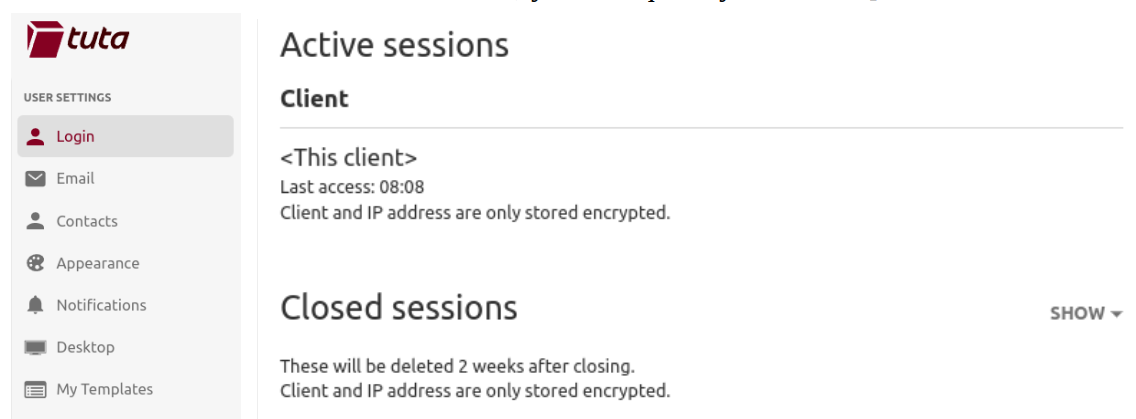

By choosing an email provider that encrypts your data you are protected against data breaches and with our easy-to-use session management tools, you can keep tabs on who has access to your account with two simple clicks. For maximum security, we advise all users to activate two-factor authentication and to write down the recovery code somewhere safe.
Tuta is making privacy and security easy and intuitive! If you haven’t signed up for your free account, you can get started today.