Security measures to look out for in a secure email service.
Secure email is important to protect your online identity. Learn which security measures are essential.
As online risks such as data breaches are steadily increasing in scale and number, it is no surprise that secure email services are seeing an influx of new users.
At the same time, every email service now stresses how secure and how privacy-friendly they are. This post summarizes a number of security measures that - in our opinion - are a minimum requirement for any email service to qualify as secure.
Secure email & must-have security measures
End-to-end encryption
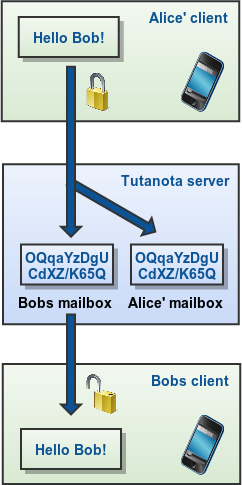
One of the most important requirement is end-to-end encryption. Any data that is not end-to-end encrypted can be accessed by the email provider - whether it claims to be secure or not. Only end-to-end encryption protects your data from the provider, and, thus, from other third parties. Only very few services encrypt your entire mailbox.
Sending an end-to-end encrypted email only works if both people in a communication use encryption. Known encryption methods are PGP or S/MIME. The difference to a normal email is that with end-to-end encryption enabled, the data gets scrambled locally on the device of the user and is only put together into readable text on the device of the recipient. Anyone tapping in on the communication in-between will only see unreadable, scrambled data.

To PGP or not to PGP
At Tutanota, we deliberately chose not to encrypt emails with PGP. We use the same algorithms - AES and RSA - but with our own implementation.
The reasoning behind this is that PGP lacks important requirements that we plan to achieve with Tutanota:
-
PGP does not encrypt the subject line (already achieved in Tutanota),
-
PGP algorithms can’t be easily updated,
-
PGP has no option for Perfect Forward Secrecy,
-
PGP can only be used for email communication.
To keep email encryption easy and secure for everybody, the model of the future can not depend on PGP for several reasons:
-
Key management must be automated.
-
It must be possible to automatically update encryption algorithms (e.g. to make the encryption resistant against quantum computers) without the need of involving the user.
-
Backward compatibility must be stopped. Instead, all systems must update within a very short time-frame.
-
Forward secrecy must be added to the protocol.
-
Metadata must be encrypted or at least hidden.
This is what we at Tutanota have been working on these last couple of years: An easy-to-use email client that has baked encryption into the software and that lets users easily encrypt any email end-to-end.
Two-factor authentication

Two-factor authentication can be easily summarized as
- Something you know, like a username and password, and
- Something you have, like your hardware key or your mobile phone
Any email service that claims to be secure must offer a way to protect your login with two-factor authentication, best with Universal 2nd Factor (U2F) authentication.
Most secure: hardware key (U2F)
The two-factor authentication method U2F is the most secure method for 2FA: You own a hardware key or hardware token, and you need to physically use this key to access your account.
It is the best protection against email phishing. Even if malicious attackers were able to phish your password, they would still not be able to access your account as they do not have access to your physical key.
Secure and easy: TOTP
Another option for two-factor authentication is using a TOTP app such as andOTP from F-Droid. These apps are downloaded to your phone and generate a code that you need to enter upon login.
Open source
Any email service can claim that they are securely encrypting your data or protecting your login credentials. Security experts can only verify that these claims are true and that there is no encryption backdoor if the entire client code that runs the service is published as open source. This is what makes an open source email service so much more secure than a closed source service.
We at Tutanota publish all clients as open source on GitHub. The most secure way to use Tutanota is to run the open source desktop clients. These clients run the code that is published on GitHub, and you can verify that the published code is being run by checking the signature.
Privacy protection
Email in general is a very insecure protocol. A standard email sends a lot of information along in the header, for instance your IP address, which is not really necessary. If you load external images, the sender of an email can include tracking pixels in these images. By loading them, the sender knows what IP address you have, where you are, what browser you are using and more.
For that reason, any secure email service should make sure that your privacy is protected as good as possible. Important privacy-protecting measures are:
- stripping of metadata (header)
- blocking image loading by default
- not logging IP addresses of users
These features are oftentimes not supported by major email services. If you care about your privacy, now is the time to leave Gmail and other privacy-invading services.
Server location
Until a few years ago, server location was not considered as a security requirement. However, the country where a server is located can usually get access to the data held on the server. What is more, the authorities of Australia, Great Britain, Canada, New Zealand, and the United States closely cooperate to share data about citizens, gathered from servers in their countries.
It is, therefore, important that the country of the server location has laws that protect citizens’ data. Germany, for instance, has very strict data protection laws and must also abide by the GDPR. Data stored on German servers can only be requested by the authorities with a valid German court order, which has to be issued by a German judge.
How to choose a secure email service
Most, but oftentimes not all, of the features discussed above are supported by so called secure email services. To check whether your favorite service supports all security measures, please check these comparisons about Protonmail vs Tuta Mail, ProtonMail vs Gmail, and Mailbox.org vs Tuta Mail.

