Which is the most secure email service?
All-round encryption, no tracking, open source - there are lots of factors that make Tutanota the most secure email provider in the world.
When checking the security and privacy of any online service, always ask yourself the following questions:
-
Who pays for it? The users or the advertisers? If the answer is “the advertisers”, the service can never offer a truly secure and private solution. Its top priority is the happiness of advertisers, usually by offering them access to user profiles. Protecting users’ privacy must always come second with such a business model.
-
Who controls the tech stack? This is a very technical question, nevertheless, it is of crucial importance. If a service uses third-party ‘tech’ such as Postfix, Dovecot, Roundcube, Google reCaptcha or Google Push, you can know for sure that security and privacy can not be its core priority as the provider knowingly leaks information to others - without warning the users about this.
-
What data is end-to-end encrypted? Many email providers claim that the data stored with them is ‘encrypted’. What makes this question so important is how is the data encrypted? Because only when data is encrypted end-to-end, it is truly inaccessible to the online service as well as to other third parties. That’s why simply “encrypting” data is not sufficient, the data must be encrypted end-to-end.
Now that we know what to look for in the most secure email service, let’s take a look at who ticks all the boxes!
What makes an email provider “the most secure one”?
Based on the questions discussed above, there are many factors that need to be considered when deciding whether an email service is the most secure one or not.
Factors defining level of security
- Control of the software stack
- Encryption of all data
- Privacy protection
- Focus on open source
- Best login protection
- Securing the email protocol
- Zero-knowledge calendar
- Post-quantum secure encryption
1. Control of the software stack
Many email services use third-party tech to build their own service such as Postfix, Dovecot, Roundcube and so on.
Every time a so called secure service uses third-party applications, it becomes more difficult to secure said service.
Of course, we at Tutanota can’t re-invent the wheel either. But we have built our entire clients - web, Android, iOS, and all desktop clients on our own.
Check here why we recommend to choose our secure desktop clients for Linux, Windows and macOS and why it is so important that we have built our own open source captcha.
One main differentiator of Tutanota is that we build all major parts of Tutanota ourselves. Besides that, we also make sure that the open source tools Tutanota does use are secure ourselves: We regularly commence security reviews of these tools as well as of our own clients, for instance when we pushed our desktop clients out of beta.
Only with open source - of our own clients as well of the software that Tutanota depends on, tech-savvy people can audit the code and verify that Tutanota is doing what we promise: Securing your private emails to the maximum.
2. Encryption of all data
Tutanota is the world’s most secure email service because we protect your data at all ends. Whether on our servers, or on your devices: In Tutanota all data is always end-to-end encrypted.
When offering a secure email service, people trust that you do security right. To us, this means that there can never be a compromise when it comes to security.
Security must be baked into the code so that you can easily add usability on top of that - not the other way around.
This concept of “security first” has led to several development decisions that today guarantee the top-notch security of Tutanota:
-
We do not use PGP, but a slightly different implementation of AES and RSA, which lets us encrypt much more data (subject lines) as well as encrypt all other features that we add to Tutanota such as contacts and calendars - which both are 100% encrypted.
-
We do not search your data on the server because it is encrypted there. Instead Tutanota builds an encrypted search index, which is stored locally and searched there. This enables Tutanota to search your entire emails (sender, recipient, subject line, body, attachment) locally while protecting your privacy.
-
We do not offer IMAP as it would only work if we sent decrypted data to your device. Instead we have built our own open source desktop clients, which store your data encrypted. The desktop clients are also signed so that everyone can verify that the client is running exactly the same code as the code published on GitHub.
End-to-end encrypted
From the start, we at Tutanota baked end-to-end encryption into the code. Tutanota was the world’s first end-to-end encrypted email provider and, to this day, it is the email service that encrypts more data than any other.
You can check here all the data that Tutanota encrypts:
- Emails, including subject lines and attachments
- Calendar entries, even metadata such as who is attending
- Entire address book, not just parts of the contacts
Tutanota automatically encrypts all emails between Tutanota users end-to-end, which makes a great difference to online security as a whole. Tutanota even lets you send end-to-end encrypted emails to anyone.

We never send unencrypted data
Whenever you communicate with Tutanota - receive a notification about a new email, execute a search, enter a calendar entry, add a new contact to your address book - your data is always sent end-to-end encrypted. We never send unencrypted data via notifications, and we never allow that unencrypted data is stored on your device.
Even when you search your encrypted mailbox in Tutanota, the search index is encrypted and stored locally before you can safely search your data.
3. Privacy protection
Anonymous email
Our business model is different from most email services: Due to the encryption, we can not scan your emails and we do not track you. We do not send targeted advertisements to your mailbox.
By default, Tutanota does not log IP addresses when you login or when you send an email. Upon registration you do not need to provide any personal data (e.g. when registering an email account no phone number is required), even when you register via Tor.
Tutanota strips the IP addresses of emails sent from the mail headers so that your location remains unknown.
No tracking allowed
Obviously, Tutanota itself does not track you when using Tutanota.
On top of that, Tutanota blocks tracking by not loading images automatically. This is important because email is the favorite tool of marketers who want to track everything you do online.
Emails let marketers track you by including tracking pixels which show the sender who opened an email when, whether they clicked the links contained, and more. These tracking pixels are external content in an email, which must be loaded.
If a mail client loads external content such as images automatically, these tracking pixels are loaded as well. Tutanota blocks this to make sure that you only load external content when you actively agree with being tracked by the sender.
4. Focus on open source
We have published all email clients as open source so that security experts can check the code.
This way we make sure that there can never be an encryption backdoor in Tutanota.
Along with this focus on open source, we do not use any Google services, such as Google Push (FCM) or Google reCaptcha, to make sure that this Silicon Valley giant can not track you while checking your secure mailbox or your encrypted calendar.
5. Best login protection
Tutanota lets you create the most secure password by enabling you to choose a password as long as you would like it to be.
We never transmit your password to the server, but only send a hash. Because it is impossible to derive the actual password from this hash, we can never get hold of your password.
We also enable all users to activate two-factor authentication (2FA) with a hardware token (U2F) or with an authentication app (TOTP).

When it comes to resetting passwords, Tutanota has chosen the most secure way: Only the users can reset their passwords with their recovery codes. This is crucial because other methods to reset passwords, e.g. sending a password reset email, are prone to targeted attacks that would enable third parties to take over accounts maliciously. As a secure email service, we must make sure that our users’ accounts can not be stolen with such simple methods.
Check here why our system is the most secure password reset option. To maximize your own login protection, we also recommend reading our email security guide.
We also strongly recommend to use a password manager to make sure you never lose your password and recovery code.
6. Securing the email protocol
When sending emails with Tutanota, you have clearly chosen the most secure option as Tutanota allows to automatically encrypt emails end-to-end.
However, sometimes it is necessary to send and receive unencrypted emails. It is much harder to secure these emails because in such a case the email provider can only encrypt the transmission - not the data itself. Besides that, other services are part of the sending process that also need to make sure that the transmission is completed securely, for instance, the receiving provider.
To secure unencrypted emails as well as possible, we adhere to highest possible standards of the SMTP email protocol.
Tutanota supports MTA-STS. This standard should be supported by all email services by now because it is to an email what strict HTTPS is to a website: It enforces transport encryption (TLS) whenever TLS is possible.
Tutanota also supports SPF, DKIM and DMARC. These three protocols are necessary to harden the infrastructure against intrusion from phishing and spam emails. SPF, DMARC and DKIM are also supported for your custom domain emails.
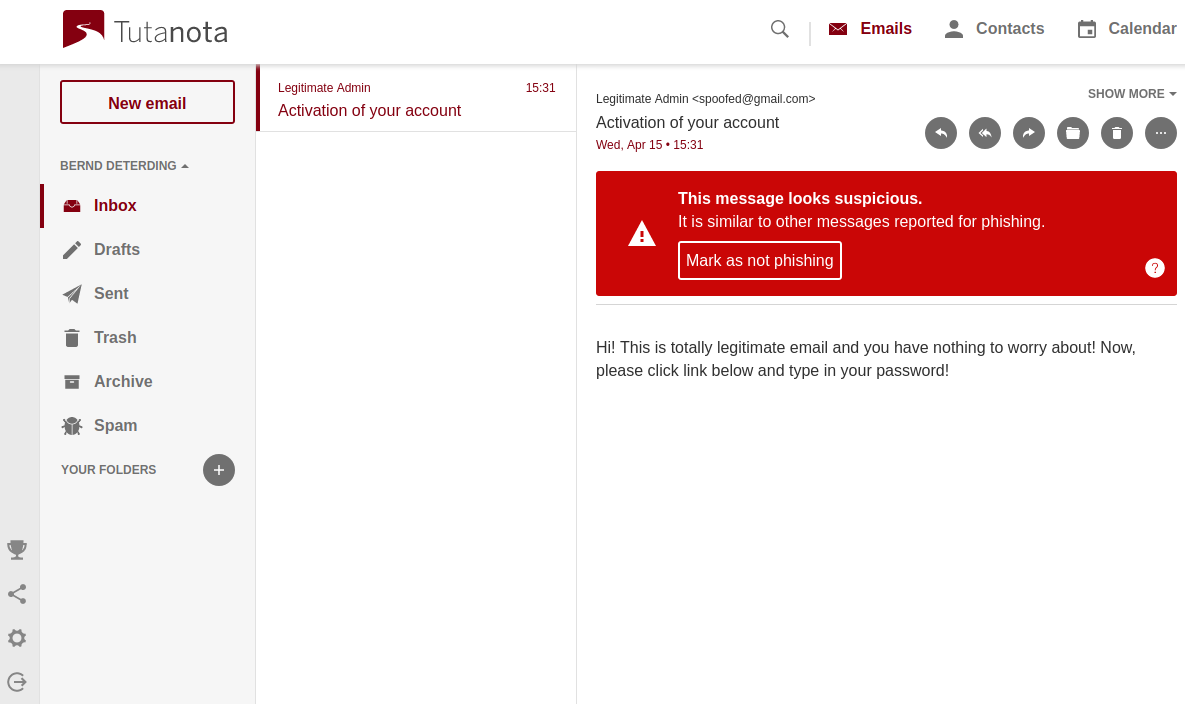
Tutanota adds another layer to this protection by enabling its users to report phishing emails. This reporting features works with zero-knowledge as well:
When an email is reported, we create signatures from it (hashes of different fields). When another user logs in, these signatures are downloaded. When you open an email, Tutanota calculates hashes of different email fields and compares them to the downloaded ones that have been reported. This happens locally on the client. If there are enough matches, the email is considered as phishing and marked accordingly.
As you can see from this example: We take your privacy seriously in every step - even when reporting potential phishing emails. We do not even want to see these emails in clear text as the reporting might have happened accidentally.

7. Zero-knowledge calendar
We have built the first end-to-end encrypted calendar. The Tutanota calendar encrypts all data, even the attendees of an event are stored encrypted.
The calendar is the only zero-knowledge calendar out there because even when you get a push notification for an upcoming event, we have built this reminder service in such a way that our servers never see the notification. This will keep our servers in the dark not just about what event you have, but also when your events are taking place.
Any calendar having email notifications - even when encrypted - can’t be considered zero-knowledge. That’s why we have gone to great lengths to push encrypted notifications directly to the Tutanota clients, for instance to our desktop and mobile apps. The big plus with the mobile apps is that you also receive these reminders when you are not actively using the app.
Check our post about our first release of the calendar to learn why encrypted notifications are so important to protect your privacy.
8. Post-quantum secure encryption
Tutanota is not only the most secure email service at the moment, we also plan to stay the most secure one in the future.
That’s why we have already started to work on post quantum secure encryption. We launched the PQ Mail project in 2020 and by now we have a working prototype that lets us encrypt emails with a hybrid protocol combining our proven encryption algorithms with post quantum secure algorithms.
In this post we explain why we need quantum-resistant cryptography now. A little hint: It is necessary to stay ahead of the NSA and others who want to use quantum computers to decrypt past communications.
Fighting for your right to privacy
At Tutanota we are committed to fighting for your right to privacy with technology. We want to make sure that mass surveillance as well as surveillance capitalism becomes impossible by applying end-to-end encryption to all data possible.
Enjoy the most secure email provider Tutanota by signing up now
Together we will make the internet more secure.