What is end-to-end encryption and why it matters.
End-to-end-encryption: Your key to keeping your data private and secure.
End-to-end encryption is becoming more popular than ever. One main reason for the success of end-to-end encryption is that major services around the world are now using some form of end-to-end encryption: WhatsApp, Signal, Threema, and, of course, also Tutanota encrypt your data end-to-end. And the best part here is: The encryption takes place automatically so that you do not have to be tech-savvy to secure your communication.
Nevertheless, there is still a lot to learn about encryption and why it matters. So let’s dive right into it.
In this video we demonstrate how easily Tutanota encrypts your emails. If you’d like to try this out for yourself, sign up now!
As a beginner in cryptography, we would recommend looking at our post about cryptography basics, which lays the foundation for understanding end-to-end encryption.
What is end-to-end encryption?
End-to-end encryption renders any form of data (text, documents, files) from a readable format into an unreadable format. In consequence possible eavesdroppers can only get hold of unreadable, scrambled data, which they can not decipher. Only the recipient can decrypt the data with the help of the matching decryption key.
When end-to-end encryption is applied, no third party can read the encrypted text, not even telecom providers, internet providers, or the provider of the communication service itself (for instance the email or messaging services).
In other words: If an email provider (such as Tutanota) offers end-to-end encryption, only you and the person you are communicating with will be able to read the contents of your messages. In this scenario, not even the company operating the email app can see what you are sending and receiving.
How does end-to-end encryption work?
On a technical level, every public key matches to only one private key (= public key cryptography). These keys are used to encrypt and decrypt messages. If you encode a message using a person’s public key, they can only decode it using their matching private key.
When the data is being encrypted, it is changed into an unreadable format. From then on, any third party getting hold of the data will not be able to decrypt the encrypted data, let alone read the messages sent. Only the intended recipient can decrypt the data and transform it back into a readable format.
This is called asymmetric encryption. Oftentimes asymmetric encrypted systems (such as PGP or Tutanota) use the algorithms AES and RSA. However, it is likely that this asymmetric encryption will become breakable once quantum computers are being developed. That’s why we at Tutanota are already working on implementing post-quantum secure algorithms to future-proof the encrypted data.
When do I need end-to-end encryption?
End-to-end encryption is needed whenever you want to send a confidential message. That is whenever your message contains personal or sensitive information that should not be seen by any third party.
What is the difference between an end-to-end encrypted email and a normal email?
Emails that are sent end-to-end encrypted can only be read by the sender and the recipient. Emails that are not sent with end-to-end encryption are still protected with transport encryption such as TLS. However, if third parties such as state agencies, malicious attackers, or even the email provider itself intercepts these emails, they are available in clear text and easily readable.
The following examples show the difference between end-to-end encrypted, confidential emails and emails that are not being end-to-end encrypted in Tutanota.
Alice is registered with Tutanota, Bob may be registered with Tutanota or may be an external recipient and Carol is not registered with Tutanota. In any case all emails (including attachments) are stored encrypted on the Tutanota servers. Independent of the end-to-end encryption, the transport between your client and the Tutanota servers is secured with TLS to maximize security.
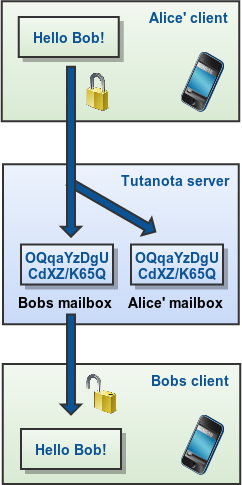
Sending and receiving of end-to-end encrypted emails
The email is encrypted on Alice’s client, stored encrypted on the server and can only be decrypted by Alice or Bob.

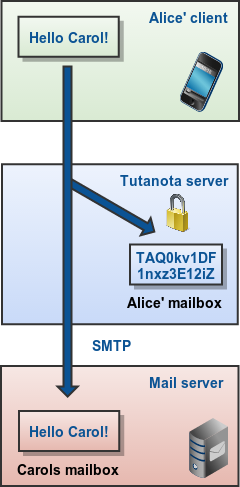
Sending of non-confidential emails
The email is sent via SMTP (Simple Mail Transfer Protocol) to the recipient. Still, the sent email is encrypted for Alice on the server and then stored.

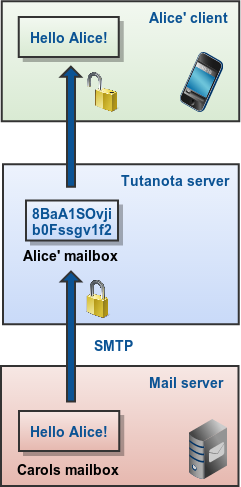
Receiving of non-confidential emails
When an SMTP email is received by the Tutanota server, it is encrypted for Alice and then stored on the server; but before that it travelled across the web without end-to-end encryption.

What data can be encrypted end-to-end?
Originally end-to-end encryption was all about communication, most notably via email with PGP encryption. One reason for this is that PGP was the first system that enabled people to communicate via email in an end-to-end encrypted format.
However, due to the complexity of PGP, it never reached the mainstream - despite its popularity as such. Today, lots of providers from email services to chat apps offer automatic end-to-end encryption, which makes switching to encrypted communication much easier for everyone.
On top of that, there are now also end-to-end encrypted applications, like Tutanota’s encrypted calendar that have nothing to do with communication. While here the upload of the data and the download of the data is always the same person (not two like with email or chat communication), the data is still end-to-end encrypted: It is encrypted on the user’s device, then uploaded to the provider’s servers in encrypted form, and can only be decrypted on the user’s device after the download.
So today, end-to-end encryption does not have to involve communication. Any data - calendars, notes, drive, password managers, but of course also email and chat messages - can be end-to-end encrypted.
Who holds the key?
The most important question with encryption is always: Who holds the key? Many providers - even Google - encrypt users’ data on their severs to protect them from malicious attackers. However, in most cases the provider itself holds the key and, thus, can easily decrypt the data - whether its documents, files, emails, calendar events, pictures, or anything else. This so called encryption ‘at rest’ can not be defined as end-to-end encryption.
When a provider only encrypts the data at rest and not end-to-end, there are a lot of ways someone could get hold of your data:
If a rogue employee wanted to snoop on your data, the encryption wouldn’t stop them.
If a malicious attacker somehow compromised the provider’s systems and private keys, they would be able to read everyone’s data. The likelihood of this, however, is rather small, depending on how well the provider’s system is set up.
If the provider was required to turn over data to a government, they would be able to access all of your data and hand it over to the authorities.
Only when end-to-end encryption is applied, the provider can not decrypt any of the users’ data. That’s how Tutanota does it: We encrypt all user data end to end so that we can not access your encrypted data stored in your mailbox. Even if you receive a not-encrypted email, we can not decrypt it once it is encrypted with your public key. As we do not have access to your private key, only you can decrypt your data.
This brings us to our last questions: Why does encryption even matter?
Why encryption matters
Only end-to-end encryption offers true privacy.
Only when data is encrypted end to end, you can be sure that no one else is listening in - whether you communicate with others via encrypted chat apps like Signal or Threema or via encrypted email like Tutanota.
Encryption enables you to communicate privately online. It is like having a private conversation in person, or whispering into someone’s ear - but on the world wide web.
While we would never question a private conversation in person, some state actors like to present encrypted conversation online as something suspicious, something that is used primarily by criminals to plot their evil schemes.
That is why the crypto wars are still ongoing.
However, a private conversation online must be perceived as just that: a private conversation. Lots of citizens like to keep their private thoughts and conversations private. We must remember that by doing so, they not only protect their communication from state agencies, but also from criminals online that want to abuse their data, e.g. for identity theft.
By demanding backdoors - as done in the cryto wars - politicians are not asking us to choose between security and privacy. They are asking us to choose no security - as we explain here.
After all, a lot of people - journalists, activists, whistleblowers, but also politicians, lawyers, medics and lots of businesses - depend on encryption to share their sensitive data in a private and secure way.
Encryption matters.



