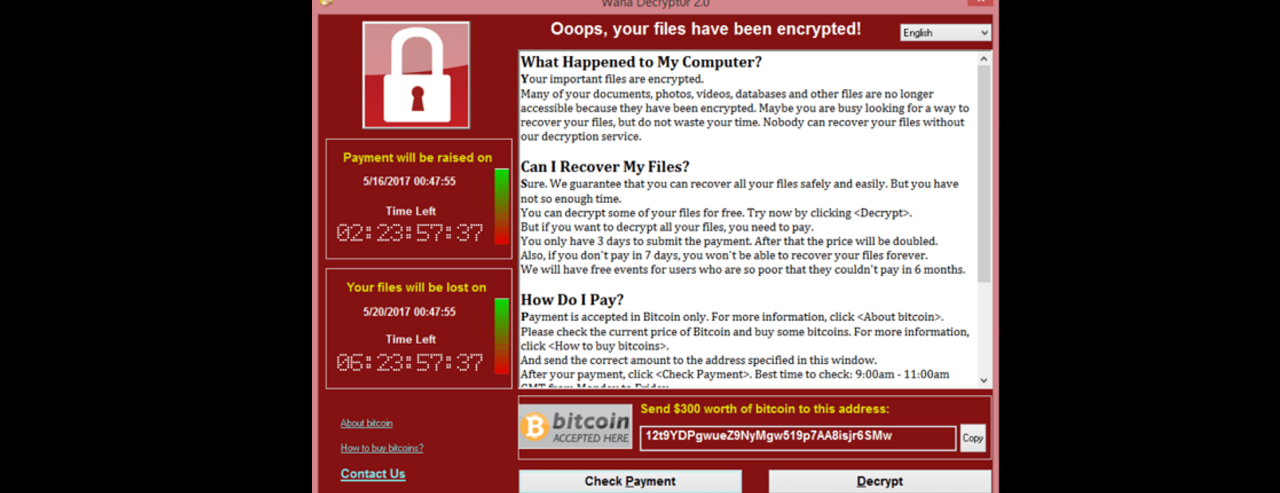
WannaCry Ransomware - Why NSA and Microsoft Are to Blame.
After the WannaCry ransomware attack - also called WanaCrypt0r, WeCry, WanaCrypt or WeCrypt0r - has encrypted files on thousands of computers asking for a $300 ransom to be paid in Bitcoin, Microsoft has now released a patch that can protect computers from Wannacry. (Scroll down to get more information on how to patch your Windows system.)
How WannaCry was able to affect 200.000 computers
The ransomware attack WannaCry was spreading like a virus over the last weekend because so many systems were vulnerable to the attack. If your computer hasn’t been affected so far, the above will help to protect your computer against WannaCry.
Since many computers are still vulnerable, WannaCry is still spreading. It exploits a security hole in the Windows SMB server that allowed the virus to spread within a private network once it has infected one machine. The first step in this attack was to send a malicious file, ie. a compressed file via mail attachment or Facebook chat to one person. Once they opened this attachment the first machine was infected and WannaCry was ready to spread through the Windows SMB server.
The NSA and Windows are responsible
The ransomware WannaCry was spread by criminals. However, the NSA and Windows can definitely be hold responsible for the scale of the attack. Here’s what the NSA and Windows did instead of closing the vulnerability right after its first discovery:
-
The NSA had known about the vulnerability in Windows for a long time. Instead of informing Microsoft they developed the exploitation tool EternalBlue. They didn’t inform Microsoft about this because they wanted to use the exploit for their own purposes.
-
Then the exploit was stolen from the NSA by a group of hackers calling themselves “Shadow Brokers” who sold it on the dark web.
-
It is assumed that only then the NSA informed Microsoft about the vulnerability and Microsoft developed a patch, but only for supported systems and for people and companies paying the support fee.
-
Only when the scale of the attack became visible on May 12 Microsoft published a patch for all versions of Windows - even for the unsupported ones.
NSA & Microsoft won’t protect you in the future
With the way they handled this severe security threat, the NSA and Microsoft have shown that the security of online users are not their prime interest.
The prime interest of Microsoft is to protect paying customers only. Microsoft could have published the severe danger of the WannaCry threat much earlier, providing a patch alongside with a call-to-action to ALL Windows users - also to the ones using outdated versions of Windows. Instead they chose to remain silent, only providing a patch when it was too late for many.
A backdoor is a backdoor is a backdoor
To sum up: What the NSA and Microsoft have done here is leaving a backdoor to Windows open so that malicious attackers were able to exploit the vulnerabilty. This led to a cyber attack so large it has never happened before. This should be a lesson to politicians, especially in the US and in the UK who regularly call for backdooring encrypted applications.
There is no ‘good’ backdoor. Any backdoor can and will be exploited by bad guys. This is the main lesson all politicians have to learn from the WannaCry attack. And we - as Internet users - have to constantly remind them!
This should cut any government request for backdoors short. Any backdoor can & will be exploited eventually.https://t.co/8LgbUqrGcO
— Tutanota (@TutanotaTeam) May 12, 2017
We believe that end-to-end encrypted services such as our secure email service is much needed to protect everybody’s right to privacy online. We would never allow a backdoor in Tutanota.
We call for an open source approach to secure the Internet
The whole WannaCry affair leaves us - the Internet users - in a difficult position. We cannot trust any closed source application to be free from vulnerabilities. Even when security experts find vulnerabilities in these applications - like the experts working for the NSA did - there is no guarantee that the vulnerability is going to be fixed.
That’s why we call for an open source approach to secure the Internet: When the code of an online application is published as open source, it is much more likely that someone else - not just the NSA - will find a potential vulnerabilty and directly inform the developers about this.
That’s why open source software is much more secure: More people look at it, more people find vulnerabilities, and the pressure to publish the vulnerability after it has been fixed is also much higher.
That’s why we at Tutanota strongly support the idea of open source. Tutanota’s client is published as open source on Github where it can easily be audited by security experts.
If Windows had been open source software, we are sure that the vulnerability would have been found, fixed and published years ago.
Lessons learned
Our conclusion after the WannaCry attack is that we can trust neither the authorities nor huge internet companies anymore. It is simply not their prime interest that we are using the most secure Internet possible.
If you want to change the Internet for the better stop using services that are more interested in harvesting your data. Use privacy-oriented services, preferably with built-in end-to-end encryption.
Which Windows version is affected
-
The newest version - Windows 10 - is not affected. However, all earlier versions of Windows have been vulnerable to the WannaCry ransomware attack.
-
Microsoft has earlier patched the versions Windows Vista, Windows 7, and Windows 8.1. Users of these Windows versions need to update their system to protect themselves from WannaCry.
-
Users of Windows XP, Windows Server 2003 and Windows 8 need to get the patch from the Microsoft website.