Google introduces new security requirements for bulk email senders - but should have done so years ago.
Google and Yahoo! will require the use of DMARC, SPF, and DKIM in an attempt to crackdown on spam and phishing. It is surprising that these features were not already a requirement.
Google has announced that they will begin enforcing stricter security measures for all accounts which are sending more than 5000 emails per day to personal Gmail users. This change comes as an attempt by the Big Tech email provider to crack down on phishing emails and spam targeting users of their Gmail service. Gmail is the world’s most popular email provider and also a major source of the world’s spam emails. As part of these new measures they will be requiring so called “bulk senders” to implement previously optional security settings to their custom domain email addresses. These settings are DMARC, SPF, and DKIM, security settings which Tuta custom domain users were required to enable since 2019.
In the following article we will examine what these acronyms mean and how they can protect a custom email domain address from being abused for spam or phishing.
These include:
New Security Standards
The new security requirements which Google is introducing collectively provide different ways of ensuring the authenticity of emails. As with any area of IT there are a number of acronyms we should unpack and explain. What is important to note is that these are applied to custom domain addresses used by bulk senders who wish to send email traffic to Gmail users.
DMARC: Domain-based Message Authentication, Reporting, and Conformance
DMARC stands for Domain-based Message Authentication, Reporting, and Conformance. It is an email authentication protocol that gives custom domain users the ability to prevent others from using their domain without permission. When fraudsters send emails pretending to be a local business, this is called “email spoofing” and DMARC adds an additional check which prevents this. When a DMARC entry is added to the DNS settings panel from a domain provider, email servers receiving an email from that custom domain can authenticate the email based upon instructions set by the owner of the custom domain. If the checks are passed, the email can be delivered and if it fails the email will be rejected according to the configuration rules of the domain owner.
DMARC acts as the rule setter for deciding what kind of actions are taken if SPF and DKIM checks are not properly satisfied.
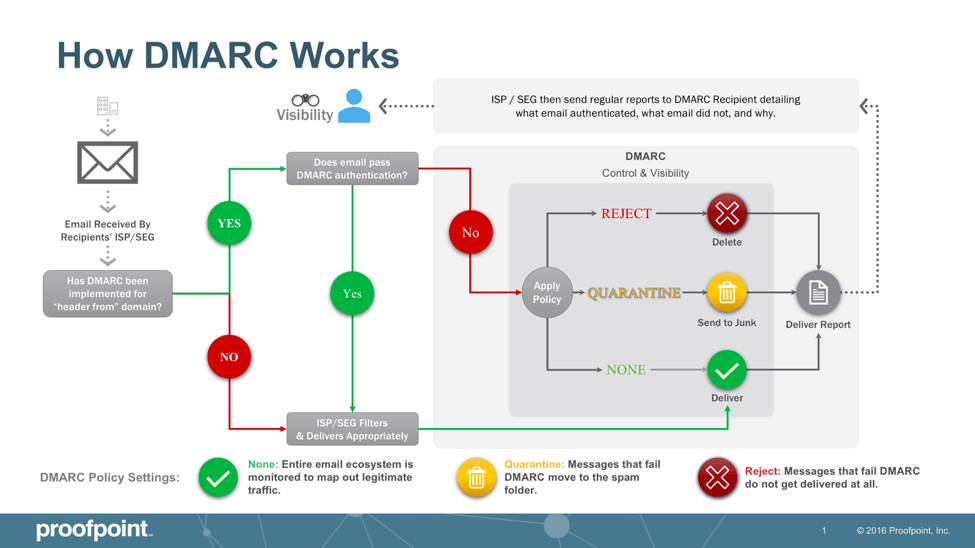

Image from ProofPoint security
SPF: Sender Policy Framework
Sender Policy Framework (SPF) is the next element in the new Google security requirements. The job of an SPF record is to authenticate that the sending email server is allowed to be the origin point for emails sent with the user’s custom domain. This element is dependent upon a correctly configured DMARC record for determining what happens if the SPF record check fails. By publishing an SPF record in your DNS records spammers and other attackers are less likely to try and use your domain because their spam emails will be unable to verify as they are being sent from a non-authorized mail server.
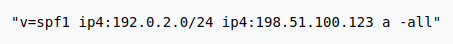

This SPF record will check to make sure that the email has been sent by one of these IP addresses, if the email was sent from any other mail server it will be rejected.
DKIM: DomainKeys Identified Mail
DomainKeys Identified Mail is the third required authentication protocol which Google will require for bulk senders. DKIM checks to prevent unauthorized use of custom domain email addresses as a counter measure to prevent phishing and email spoofing attacks. DKIM signatures are added as a means for email providers to verify the authenticity of the sender.
DKIM signing has three main steps:
- The email sender chooses which fields should be included in the DKIM signature. These can range from the “From” address, the email body, subject lines, etc. These must remain unchanged in transit or the final DKIM check will fail.
- The chosen fields will be hashed by the sender’s email provider and the hash is encrypted using the sender’s private key.
- After being sent the receiving email server will validate the signature by fetching the public key which matches the sender’s private key. This will decrypt the hash string from step 2 and verify that no changes occurred during transit.
Only when these steps are successful will the email be delivered. If they are not satisfied, the email will be rejected according to the DMARC rule of the domain owner.
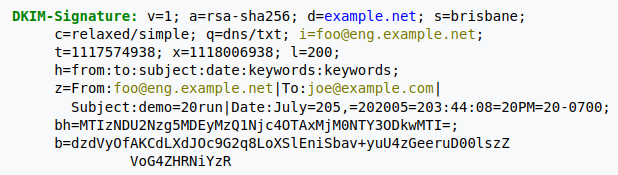

Here is an example DKIM signature used to protect a custom domain from being spoofed for sending spam or phishing mails.
Big Tech security changes are long overdue
Both Google and Yahoo! announced that these settings will be required on February 1st of 2024, but these security features have been available for years. While it is a great move by Big Tech to begin requiring these additional DNS security records, the timing is somewhat questionable. Google is without a doubt a leader in the IT security space, but their laissez-faire approach to email security seems somewhat out of place. Yahoo! doesn’t deserve much applause here either. Following major data breaches which exposed nearly all existing accounts, this traffic should have received tighter scrutiny immediately rather than nearly a decade later.
It is great to see that Google and Yahoo! are stepping up their security requirements because in 2022, nearly 49% of all emails sent were spam and need to be blocked by the receiving mailboxes.
Gmail is the leading daily spam sender at 14.5 million spam emails per day!
There is misguided criticism of privacy-oriented email services like Tuta Mail, claiming that they are a haven for miscreants and spammers. While there may be spammers who attempt to use our services, they are quickly shut down. Google’s Gmail on the other hand has been reported as being responsible for sending 14.5 million spam emails per day. The unfathomable volume of spam coming from Google’s mail servers alone dwarfs any spam attempts from other email providers.
The now in plance security measures are a step in the right direction, but in hindsight they should have been introduced much sooner.
Alternatives provide better, all-encompassing security.
Tuta Mail supports the full use of custom email domains, but during the custom domain configuration process we guide all users in how to get these crucial DNS security records added to better protect their custom domain from abuse by fraudsters. Other Big Tech providers have dropped this option, like Microsoft who recently removed this custom domain support from Outlook.
By choosing a private alternative to Big Tech providers, it is not only possible to take advantage of easy to configure domain options, but you can rest assured that your data is safe from Google’s invasive advertising practices. By choosing Tuta to protect your emails you are also protected by our world’s first post-quantum encryption. This new generation of encryption protects you and your data from intelligence agencies and their “Harvest now, decrypt later” practices.
Drop Google and choose privacy!
You deserve better than having your data scraped to train AI models which in turn push directed ads to your mailbox. You should be free to communicate securely with friends and loved ones without needing to worry about Big Tech peeking over your shoulder. By choosing a private email alternative you are protecting your freedom to express yourself.

