Faking an email sender makes a scam email appear legitimate. Since the corona pandemic scammers increasingly fake emails from the WHO.
Scam emails are a severe security risk: Phishing attacks and malware attachments are some of the biggest threats. The WHO example shows why it is so hard to get email right.
Corona crisis leads to more scam emails
Since the coronavirus pandemic, scam emails have been on the rise, including emails with spoofed email addresses.
Scammers impersonate the WHO
Increasingly, scammers send out emails that appear to come from the WHO. This is possible because the WHO has not set up their DMARC/DKIM policy strictly enough.
To be fair, it is very hard for large, federated organizations to implement DKIM and DMARC in a strict enough manner to prevent any abuse. Strict DKIM/DMARC policies in federated organizations might also lead to legitimate emails failing DKIM/DMARC checks and ending up in spam folders. Keeping up with the federated email servers can be challenging to administrators, and therefore they prefer to not set the DKIM/DMARC policy too strict.
The WHO warns everyone that they
- never ask for usernames or passwords
- never email attachments you didn’t ask for
- never ask you to visit a link outside of www.who.int
- never charge money to apply for a job, register for a conference, or reserve a hotel
- never conduct lotteries or offer prizes, grants, certificates or funding through email.
To the WHO’s defense, no big, federated organization tested - e.g. Greenpeace, Human Rights Watch, Amnesty International - did set up a strict DKIM/DMARC policy.
Setting up DKIM/DMARC is complicated
While some guides claim that setting up DKIM and DMARC would be easy, it is in fact very complicated to get it right. Nevertheless, it is very important to combat fake emails as the Australian Cyber Security Center points out.
Strict DKIM/DMARC policy in Tutanota
Tutanota has implemented a strict DKIM and DMARC policy to make sure that attackers can not spoof mails from our domains to other mail providers, such as:
- signing every outgoing email with DKIM
- including as many headers as possible on the signature
- not including the length tag, which would allow attackers to add text to the bottom of emails
We also have a DMARC policy of quarantine, which tells other providers that emails from Tutanota domains that do not have a valid DKIM signature and that do not come directly from our servers should be treated as spam.
It is a lot of work, but taking care of such things - as well as others - pays off with great results on email security checks.
Use your own domain with DKIM/DMARC
Tutanota also supports SPF, DKIM and DMARC for custom domains. With the help of our instructions, it is very easy for every Tutanota user to activate SPF, DKIM and DMARC for their own domains.
During configuration we also provide some helpful icons to show you if you have correctly configured SPF, DKIM and DMARC records.
How we spot faked emails for you
To protect our users from faked emails coming from outside:
- We have just revamped our DMARC and DKIM checking to be more secure against forgery.
- We have implemented DMARC in a way that if the domain owner has not set a DMARC policy we will use a default one that treats spoofed emails as spam.
- We are displaying these results so that you know if an email doesn’t pass a DMARC check.
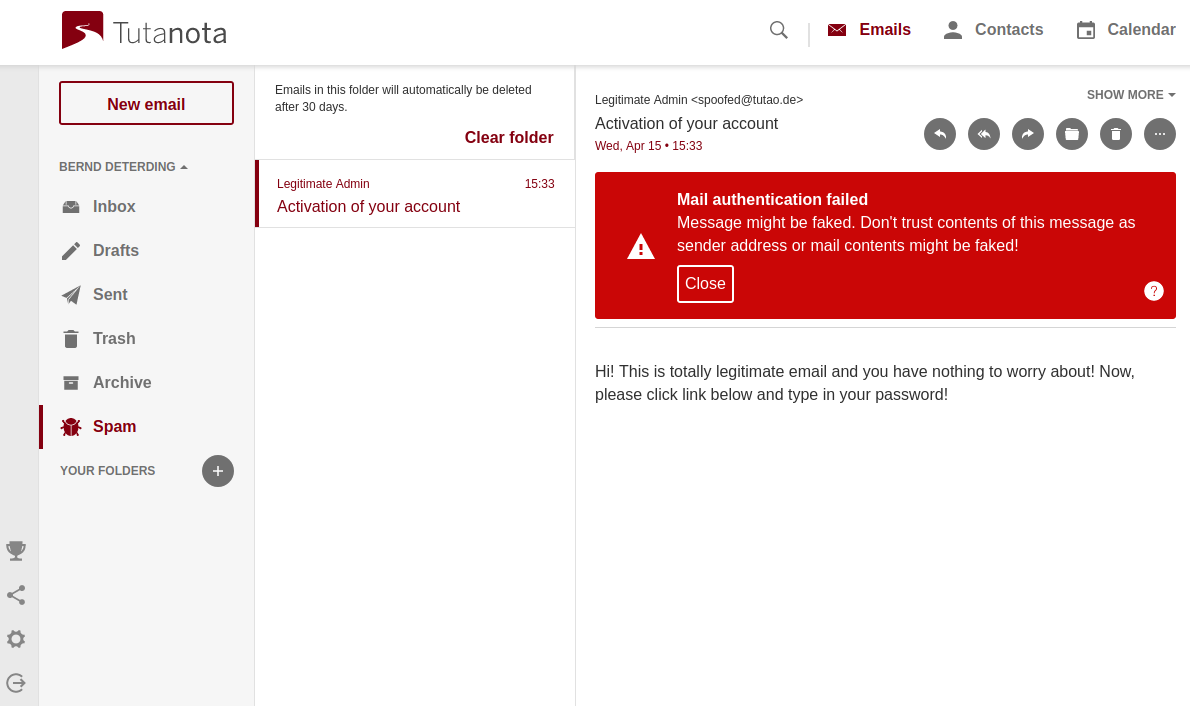

Unfortunately, we can’t block all emails that fail a DMARC check because as the WHO example described above shows this would lead to lots of legitimate emails being blocked as well.
We hope that the uptake of DMARC and DKIM will continuously increase for the security of every email user. At Tutanota, we work hard to enable all our users to only send emails with valid DKIM signatures, even when you use your own domain.
Recommended for further reading: How to prevent email phishing.

