Fourteen Eyes Countries: How does this alliance affect your privacy and security?
Five, Nine, and Fourteen Eyes Countries Explained.
Oh What Big Eyes You Have!


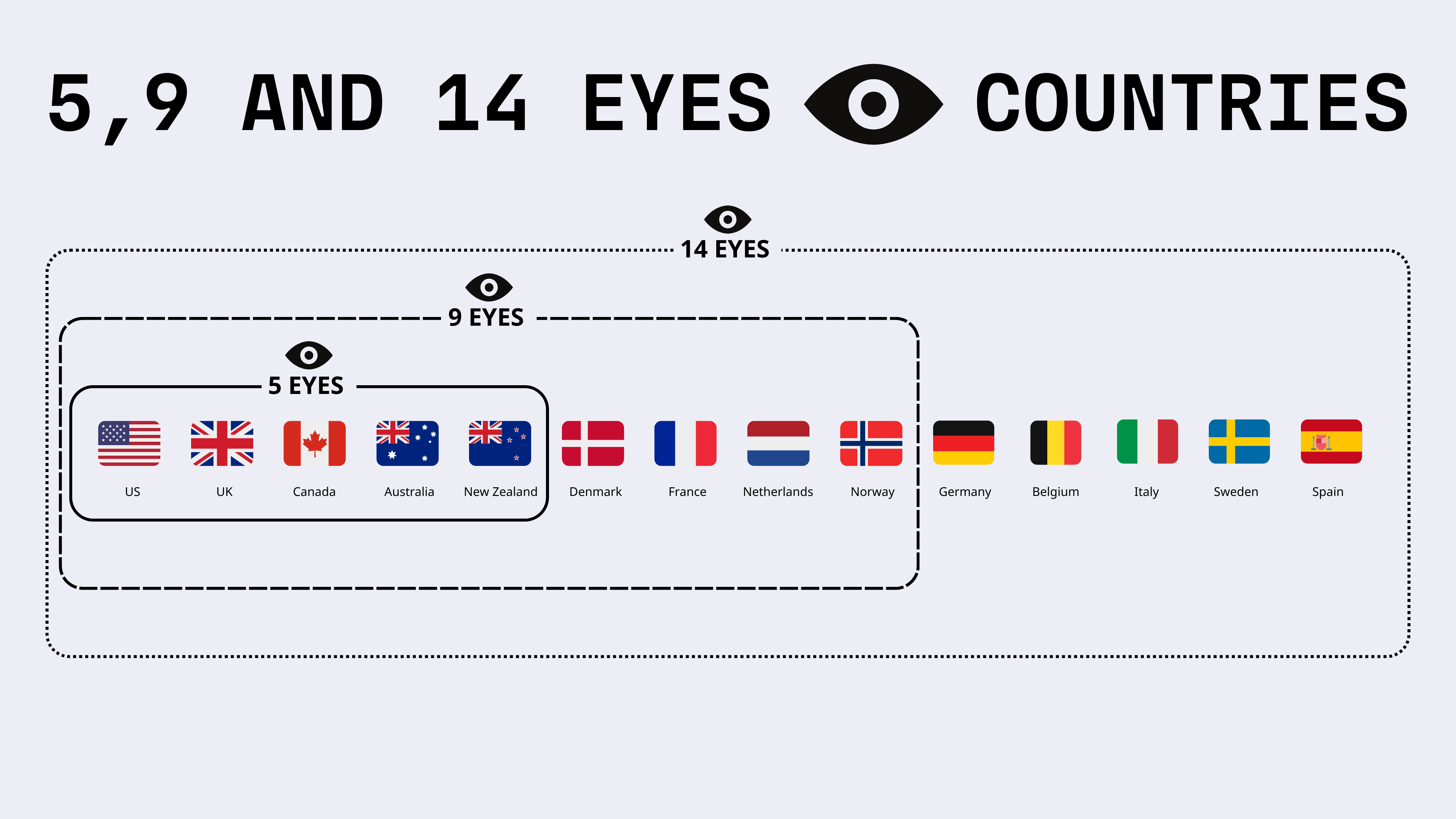
The Five eyes is made up of the US, UK, Canada, Australia, and New Zealand. The Nine eyes is made up of Denmark, France, Netherlands, Norway, US, UK, Canada, Australia, and New Zealand. Fourteen eyes is made up of Germany, Belgium, Italy, Sweden, Spain, Denmark, France, Netherlands, Norway, US, UK, Canada, Australia, and New Zealand.
Fourteen Eyes countries
The 14 eyes surveillance alliance are state intelligence services that monitor and share people’s internet activity. The US, UK, Canada, New Zealand, Australia, Denmark, France, the Netherlands, Norway, Germany, Belgium, Italy, Sweden, and Spain are part of this alliance.
But before we can begin examining the structure and operation of the Fourteen Eyes countries, we need to step back and look at the start of the current global surveillance apparatus, which has its roots in WWII. This leviathan of espionage began informally at Bletchley Park during the British and American effort to break the German Enigma Machine. The formal beginning can be found in the UK-USA Agreement which was enacted in March of 1946. The alliance quickly grew with the addition of Canada, Australia, and New Zealand.
Five Eyes countries
The intelligence alliance Five Eyes comprises the US, the UK, Australia, Canada, and New Zealand. This is one of the world’s most active multilateral agreement in which all partners monitor and share intelligence, including people’s internet activity.
The core group of national intelligence agencies are known as the Five Eyes countries (or FVEY): USA, UK, Canada, Australia, and New Zealand.
The Five Eyes spent the Cold War gathering intelligence on the Soviet Union, with different nations operating in specific global locations. Later on, other nations came to be involved in this intelligence gathering operation of the five eyes countries, and they are commonly referred to as third-parties.
It is the activity of these Five Eyes which later spawned groups like the Five Eyes Plus, Six Eyes, Nine Eyes, Fourteen Eyes, and other third-parties.
What are 5, 9, 14 eyes? List of surveillance partner countries
-
Five Eyes Countries: USA, UK, Canada, Australia, and New Zealand.
-
Five Eyes Plus Countries: Five Eyes Plus is an information sharing network between the Five Eyes, France, Germany, and Japan with the goal of countering threats from China and Russia.
-
Six Eyes Countries: Six Eyes was a failed agreement between the Five Eyes, France, Israel, Singapore, South Korea, and Japan. However the agreement fell through due to rejection by the CIA director and US President Barack Obama.
-
Nine Eyes Countries: Nine Eyes is an intel sharing partnership between the Five Eyes nations as well as Denmark, France, the Netherlands, and Norway.
-
Fourteen Eyes Countries: Fourteen Eyes is an extension of the Nine Eyes plus Germany, Belgium, Italy, Spain, and Sweden.

With all of these nations contributing and sharing intelligence, what does this mean if you live in one of these countries or store your data there?
All The Better To See You With.
We know from Edward Snowden’s global surveillance disclosures that intelligence agency’s data collection programs do not always avoid collecting data of their own citizens – even though the right to privacy is enshrined in many constitutions, such as the US constitution and the German equivalent. Surveillance of foreign targets can often snare data on a nation’s citizens during the collection process which depending on legal interpretation may be considered a violation of civil rights.
One legal “work-around” commonly employed was for partner nations to spy on interesting citizens on behalf of their host nation. This enables a country like the United States to monitor a journalist of interest by allowing another nation like the UK or France to keep tabs on the US citizen. This leaves the host nation happy, the spying nation receives information that may be of interest to them in return for their efforts, and technically no laws are broken.
Countries which don’t belong to these agreements may not receive information from this organization in the same quid pro quo manner, but nothing prevents the Five Eyes nations or Nine Eyes nations from directly monitoring online traffic.
So what can you do if you find yourself living in one of these countries or if you use an online service which operates within the jurisdiction of the Five or Fourteen Eyes countries?
The best way to protect your data from the prying eyes of nation states, hackers, insider threats, or overzealous advertising companies is to keep as much of your data as possible encrypted. By securing your data with strong end-to-end encryption, the contents of messages, images, or documents are no longer accessible. If you were to encrypt your tax documents correctly using AES-256 before uploading them to the cloud, there is a high degree of certainty that this data cannot be accessed by any unauthorized actors. This kind of encryption is so trustworthy that in 2003 the United States government made the ruling that the AES algorithm was secure enough to be used to protect classified documents. Privacy hinges upon the power of your data encryption and not necessarily just the location of your data.
Is Switzerland part of 14 eyes?


No, Switzerland is not part of the Five Eyes, Nine Eyes or Fourteen Eyes, but this does not mean that there is no surveillance. To the contrary, Switzerland is currently discussing a surveillance law that could be worse than US laws.
Many privacy-oriented services, including encrypted email provider Protonmail, like to pretend that the physical location of their services exempts them from falling into the nets of the global surveillance apparatus. One commonly cited case of a “Fourteen Eyes Free Zone” is the small nation of Switzerland.
Despite claiming that data hosted in Switzerland is more secure as the country is outside of the 14 Eyes (which is technically true as Switzerland does not belong to the 14 Eyes agreement), the Swiss Federal Intelligence Service (NDB) does monitor the communication of non-Swiss persons, just like any other secret service. The NDB uses an intelligence gathering system known as Onyx. One active collection site operated by this service can be found in the city of Leuk. The NDB also has confirmed that they maintain over 100 contacts to other global intelligence and law enforcement agencies and regularly share intelligence reports, dispelling the notion that this country has somehow isolated itself from the larger global surveillance apparatus.
While it may be that the Swiss government does not belong to any disclosed surveillance agreements, this does not exempt companies from complying with legal requests from their local authorities. This is an often overlooked course which is taken to gain information about users of online services based in Switzerland.
Foreign countries can request such information directly from the Swiss authorities, for instance via mutual legal assistance treaties such as the Council of Europe. Most recently Switzerland was a signing party to the “Second Additional Protocol to the Convention on Cybercrime on enhanced co-operation and disclosure of electronic evidence.”
This seems to cut against the popular idea that Switzerland operates as a data haven against surveillance requests.
For example, if I have an email account in Switzerland and the Swiss police presents my mail provider with a valid Swiss subpoena, they will be required to turn over the requested information. Data can also be requested by foreign agencies through data sharing agreements, which occurs regularly between global law enforcement agencies and these relationships are overlooked when claiming ‘Switzerland would be a safe haven as it is outside of the Fourteen Eyes’.
Although Iceland or Switzerland claim to be outside the reach of the Fourteen Eyes countries, both of these countries’ law enforcement agencies cooperate regularly with Europol requests which makes their services just as prone to turning over user information as any service based inside of the Fourteen Eyes.
Here’s Looking At You.
Regardless of where you or your data are located what is important is that your data is properly encrypted. By taking advantage of Tuta’s secure email platform you can rest assured that your data is encrypted both over the wire and at rest.
By using an encrypted email service, it doesn’t matter who might be trying to listen in on your conversations. This is crucial for your private communications as well as for your business email account. When you create an email account with Tuta Mail, you also get a calendar service with the same encryption and security standards, which far exceed those of any other calendar service currently available.
In the event of receiving a valid court order, data can only be turned over in its encrypted form. Without the key for decryption, which only you possess, your data is as legible as a mud puddle.
To better protect your data against future threats, Tuta Mail has already introduced post-quantum encryption algorithms which ensures that your data can resist attacks by quantum computers.
When we think about personal privacy and operational security in general, we need to create an accurate threat model for ourselves to base our privacy decisions upon. The average individual will likely never be the target of an advanced persistent threat from a nation state. For some people, the goal is to protect the unwanted spread of personal information, others may be trying to avoid a stalker or prevent doxxing.
Threat models are as unique as the person they apply to, and it is crucial that you make an accurate threat model for yourself and your privacy needs before beginning your privacy journey. The needs of a whistle blower will require a much higher degree of operational security than those of a student.
Encrypted and anonymous
Regardless, of your own personal threat model, Tuta Mail can meet your needs by providing you with a secure, easy-to-use, encrypted platform for your digital communications. Tuta Mail also allows you to sign up for an email address without a phone number to protect your anonymity.
The claim that Tuta being based in a “Fourteen Eyes country” makes its data more accessible to the authorities is simply not true. The point with Tuta is that all data is end-to-end encrypted – so not even the German Federal Intelligence Service, the BND, has access to the encrypted data stored in Tuta Mail. Thus, any data stored in Tuta can not be shared with other intelligence agencies either. Being based in a Fourteen Eyes country becomes insignificant. Protecting your online privacy is not a sprint or a one-time task, it’s a marathon. By better understanding your privacy needs and setting clear goals for protecting your personal data, you are that much closer to maintaining a healthier digital life.
What’s the issue with VPNs & how do 5/9/14 alliances affect users?
To surf the web in full privacy, many internet users turn to VPN services. These services hide the user’s real IP address from the websites and services they access. However, VPN services can not protect their users with end-to-end encryption (meaning the IP address is not encrypted end-to-end so that only the user sees it, but the VPN provider still knows the user’s real IP address) so when choosing a VPN provider location matters much more compared to choosing your email provider.
The thing is: The VPN service has access to the user’s real IP address - and can hand it out to the authorities if required by law. While many VPN providers have no-logs policies to protect their users from overzealous surveillance, the risk that ones’ identity is given to the authorities remains. So, VPN providers located in the five, nine, or fourteen eyes jurisdiction have to hand our user data upon request.
How to avoid surveillance from five and fourteen eyes countries?
Protecting users’ privacy is the mission of Tuta, and that’s why we encrypt as much data as possible with quantum-safe end-to-end encryption. To avoid mass surveillance you need to:
- Make sure that your online service encrypts as much data as possible.
- Check the jurisdiction and whether it’s part of the five, nine, or fourteen eyes alliance and whether this country has other surveillance agreements with other nations when choosing a VPN provider.
- Check the privacy policy of the services you choose and make sure these adhere to data minimization practices.
Happy encrypting, and stay safe!